Credit Card Data Being Stolen via NFC by NGate Android Malware
NGate allows attackers to clone victims' cards, enabling them to make unauthorized payments or withdraw cash from ATMs.

Introduction
Cybersecurity experts from firm ESET have discovered a new Android malware called NGate capable of transmitting victims' contactless payment data from physical credit and debit cards to a device controlled by attackers, enabling fraudulent transactions.
This activity is a part of a larger campaign targeting financial institutions in Czechia since November 2023, utilizing malicious Progressive Web Apps (PWAs). NGate was first detected in March 2024.
The attacks aim to clone Near-Field Communication (NFC) data from victims' physical payment cards using NGate, which then transmits the information to a device controlled by the attackers. This device emulates the original card to withdraw cash from ATMs.
"Good" Old Phishing
The attacks begin with malicious text messages, automated calls featuring pre-recorded messages, or malvertising, all designed to deceive victims into installing a harmful PWA on their devices.
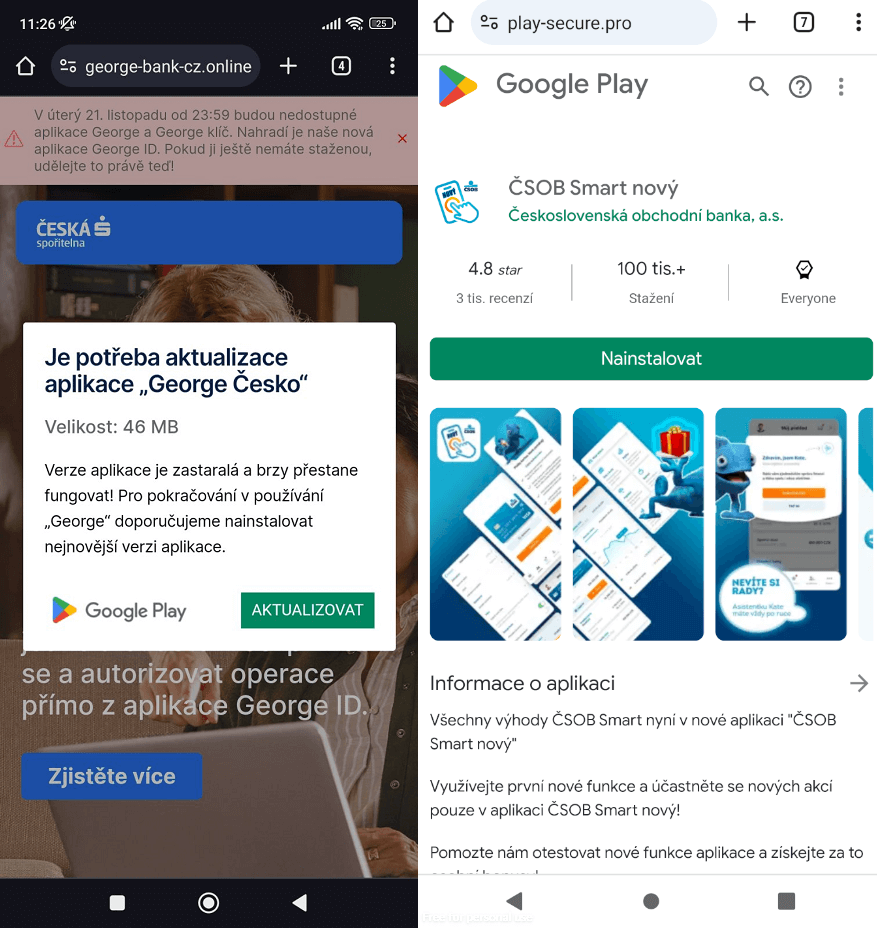
These web apps are disguised as urgent security updates, mimicking the official icon and login interface of the targeted bank to capture clients' access credentials.
See figure below: fake banking website (left) and fake Google Play website (right).
PWA apps do not require any permission when installed. They exploit the web browser's API to gain unauthorized access to the device's hardware components.
Example of a PWA icon (left) and that of the app it is mimicking (right)

Installation of Malicious Application
After the phishing phase through the PWA is completed, the victim is deceived into installing NGate as part of the second attack phase.
Once installed, NGate activates an open-source component known as NFCGate, originally developed by university researchers for NFC testing and experimentation. This tool facilitates on-device NFC data capturing, relaying, replaying, and cloning, and typically does not require the device to be rooted to function.
NGate uses NFCGate to capture NFC data from payment cards in close proximity to the infected device, transmitting the information to the attacker's device either directly or via a server.
The attacker can then store this data as a virtual card on their device and use it to replay the signal at ATMs equipped with NFC technology to withdraw cash or make payments at point-of-sale (PoS) systems (on figure bellow).
Watch ESET's video demonstrating the attack.

Malware can also clone the unique identifiers of certain NFC access cards and tokens, allowing unauthorized access to restricted areas.
Tell Me Your PIN
Most ATMs require a PIN code for cash withdrawals, which, according to researchers, is typically obtained through social engineering tactics.
After the victim falls for the PWA phishing scheme, the scammers contact them by phone, posing as bank employees and claiming there's a security issue affecting their account.
They then send an SMS containing a link to download NGate, which is presented as an app for verifying the victim's payment card and PIN.
When the victim uses the app to scan their card and enter their PIN for 'verification,' this sensitive information is transmitted to the attacker, who can then use it to make unauthorized withdrawals."
How To Stay Safe?
- If you’re not actively using NFC, you can reduce the risk by disabling the NFC feature on your device. On Android, go to
Settings>Connected devices>Connection preferences>NFCand switch the toggle to the off position. - If you need to keep NFC enabled at all times, carefully review app permissions and limit access strictly to necessary functions.
- Only install banking apps from the official Google Play.
We Can Help Protect You!
Our mobile app Redamp.io includes a Safe Surfing feature that effectively handles protection against the latest threats such as phishing or malware.
Try our application now!