Ransomware: A Growing Threat and How to Protect Yourself
In the world of cybersecurity, ransomware has emerged as one of the most damaging threats. It targets individuals, businesses, and organizations by encrypting their files or locking them out of their systems until a ransom is paid.

What is Ransomware?
Ransomware is a type of malicious software (malware) designed to disrupt access to your data or systems. It typically operates in two ways:
- Encryption Ransomware: Encrypts files on a device, making them inaccessible.
- Locker Ransomware: Locks you out of your system entirely.
The attackers demand payment, often in cryptocurrency, to provide a decryption key or unlock the system. However, paying the ransom does not guarantee recovery of your data and may encourage further attacks.
How Computers Can Be Infected with Ransomware?
Ransomware can infiltrate computers through various methods:
-
Phishing Emails : Clicking on a link in a fraudulent email redirects you to a malicious website that downloads ransomware onto your system.
-
Malicious Downloads: A free software installer may be bundled with ransomware.
-
Exploiting Software Vulnerabilities: A vulnerability in your operating system or browser is used to execute ransomware code.
-
Malicious Websites or Ads (Malvertising): A fake pop-up ad claims your system is infected and prompts you to download a "cleaner," which is actually ransomware.
-
Infected External Devices : Plugging in a compromised USB drive installs ransomware automatically.
-
Remote Desktop Protocol (RDP) Exploits : Cybercriminals brute-force their way into a system via RDP and install ransomware.
-
Software Supply Chain Attacks: A trusted software update is tampered with, installing ransomware along with legitimate files.
How Ransomware Appears on a Computer?
When ransomware infects a computer, it manifests in noticeable ways that can disrupt access to files or the entire system. Here’s what typically happens and what a user might encounter:
-
Sudden File Inaccessibility: Ransomware often encrypts files, making them unusable without a decryption key. File extensions changing to something unusual (e.g.,
.locked,.encrypted). -
A Ransom Note or Message: After encryption, ransomware typically displays a ransom note on the screen:
- An announcement that your files are encrypted or your system is locked.
- Instructions to pay a ransom, usually in cryptocurrency like Bitcoin, to regain access.
- Some ransomware includes a countdown timer, pressuring users to pay quickly by threatening increased ransom amounts over time.
- Threats of permanent data deletion or public exposure of stolen data if the ransom is not paid within a specified time.
- A contact method (e.g., email or dark web link) for obtaining the decryption key.
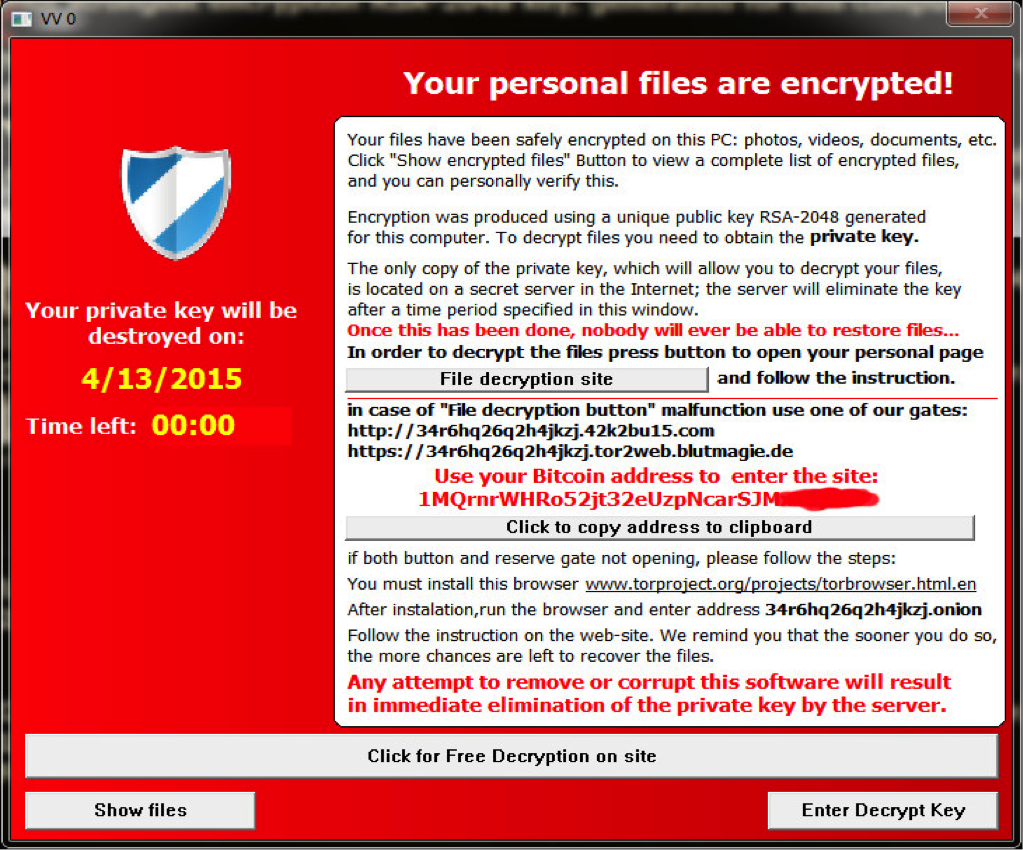
"TeslaCrypt" ransomware window with instructions:
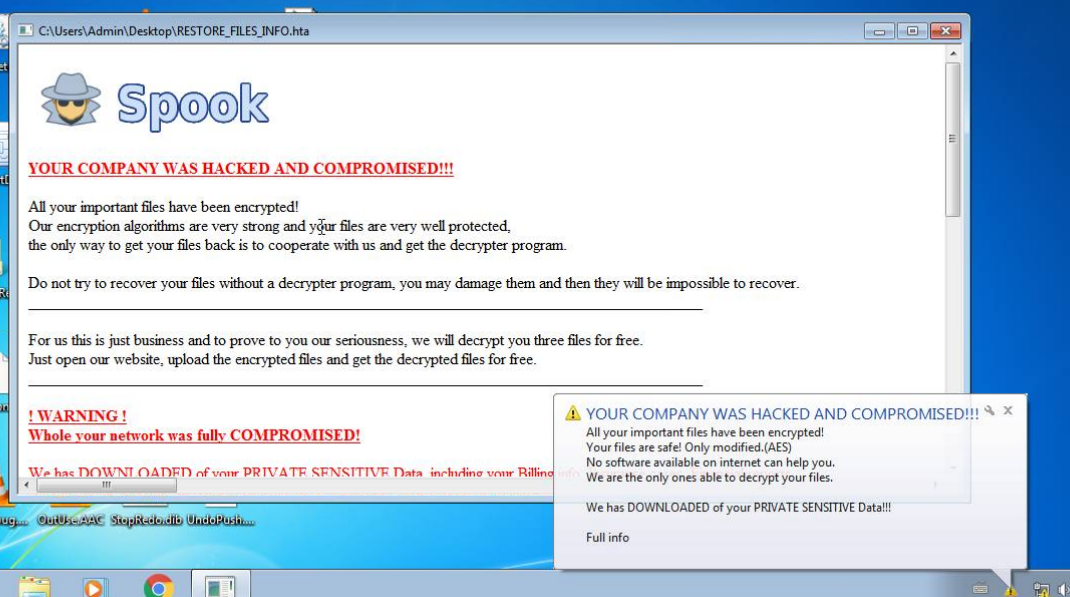
Example of "Spook" ransomware on Microsoft Windows 7 computer:
The Risks of Ransomware
The impacts of ransomware can be devastating, ranging from personal inconvenience to significant organizational losses:
1. Financial Losses: Ransom payments can range from hundreds to millions of dollars. Businesses may also face indirect costs like legal fees, lost revenue, and operational downtime.
2. Data Loss: Without a reliable backup, you risk losing important personal or business files permanently.
3. Business Disruption: For organizations, ransomware can halt operations, delay projects, and reduce productivity.
4. Reputational Damage: A ransomware attack, especially one involving leaked customer or client data, can damage trust and credibility.
5. Legal Consequences: Under data protection laws such as GDPR or HIPAA, organizations may face penalties if they fail to safeguard sensitive data.
How to Protect Yourself from Ransomware
Effective protection requires a combination of good habits, robust tools, and preparation. Here’s how you can defend against ransomware:
-
Regularly Update Your Software : Keep operating systems, browsers, and applications updated. Patch vulnerabilities promptly to close potential entry points for attackers.
-
Use Reputable Security Tools: Install antivirus and anti-malware software with ransomware detection capabilities. Use firewalls and intrusion prevention systems to monitor suspicious activity.
-
Implement Data Backups: : Follow the 3-2-1 rule: Keep three copies of your data, stored on two different media types, with one copy offline or offsite. Regularly test your backups to ensure they work and are not corrupted.
-
Be Cautious with Emails and Links: Avoid opening email attachments or clicking on links from unknown senders. Verify the sender’s email address and check for signs of phishing, such as spelling errors or unexpected requests.
-
Enable Multi-Factor Authentication (MFA): : Use MFA to secure accounts, adding an extra layer of protection beyond passwords.
-
Limit Permissions : Restrict user access to only the data and systems necessary for their role. Avoid using accounts with administrative privileges for everyday tasks.
-
Educate Yourself and Others: Learn to recognize phishing attempts and other common ransomware tactics. Conduct regular cybersecurity training for employees or family members.
What to Do If You Are Targeted
If you fall victim to a ransomware attack, acting quickly can minimize damage:
-
Disconnect the Device: Immediately isolate the infected device from the network to prevent the ransomware from spreading.
-
Do Not Pay the Ransom: Paying doesn’t guarantee your data’s return and funds criminal activity.
-
Contact Authorities: Report the attack to local law enforcement or a cybersecurity agency.
-
Restore from Backups: If you have clean backups, use them to recover your files after ensuring the ransomware is removed.
-
Consult Cybersecurity Experts: Professionals can help assess the extent of the attack and recommend next steps.
Source of images: upguard.com , blog.sekoia.io