Email has become an essential part of our daily lives, allowing us to communicate quickly and efficiently with anyone around the world. However, this convenience comes with significant security risks, especially when emails are used as logins for various online accounts.
Email as a Key to Your Online Life
When you create an account on a website or service, your email often serves as your username. This makes it a vital piece of information, connecting you to countless online platforms, from social media and shopping sites to banking and healthcare services. Because of this, your email address is a valuable target for hackers.

How Data Breaches Happen
A data breach occurs when unauthorized individuals gain access to sensitive information. This can happen in several ways:
- Phishing Attacks: Hackers trick you into providing your login credentials by pretending to be a legitimate entity, like your bank or a popular service.
- Weak Passwords: Using simple or reused passwords makes it easier for attackers to guess or crack your login details.
- Software Vulnerabilities: Sometimes, the platforms you use have security flaws that hackers exploit to access your data.
- Insider Threats: Employees or other insiders with access to data may leak or misuse it.
The Impact of Email Breaches
When a data breach involves your email, the consequences can be severe:
- Identity Theft: Hackers can use your email and associated information to impersonate you, accessing other accounts or committing fraud.
- Account Takeover: If a hacker gains access to your email, they can reset passwords for your other accounts, locking you out.
- Spam and Scams: Your email address can be sold on the dark web, leading to an influx of spam or targeted phishing attempts.
- Privacy Loss: Sensitive information, such as personal messages, financial details, and confidential documents, can be exposed.
Protecting Your Email
To safeguard your email and personal data, follow these tips:
- Use Strong, Unique Passwords: Create complex passwords and use different ones for each account. Consider a password manager to keep track of them.
- Enable Two-Factor Authentication (2FA): This adds an extra layer of security by requiring a second form of verification, such as a code sent to your phone.
- Be Cautious with Links and Attachments: Avoid clicking on suspicious links or downloading attachments from unknown sources.
- Regularly Update Software: Keep your email client and other software up to date to protect against vulnerabilities.
- Monitor Your Accounts: Regularly check your accounts for unusual activity and change passwords immediately if you suspect a breach from Privacy section of Redamp.io application.
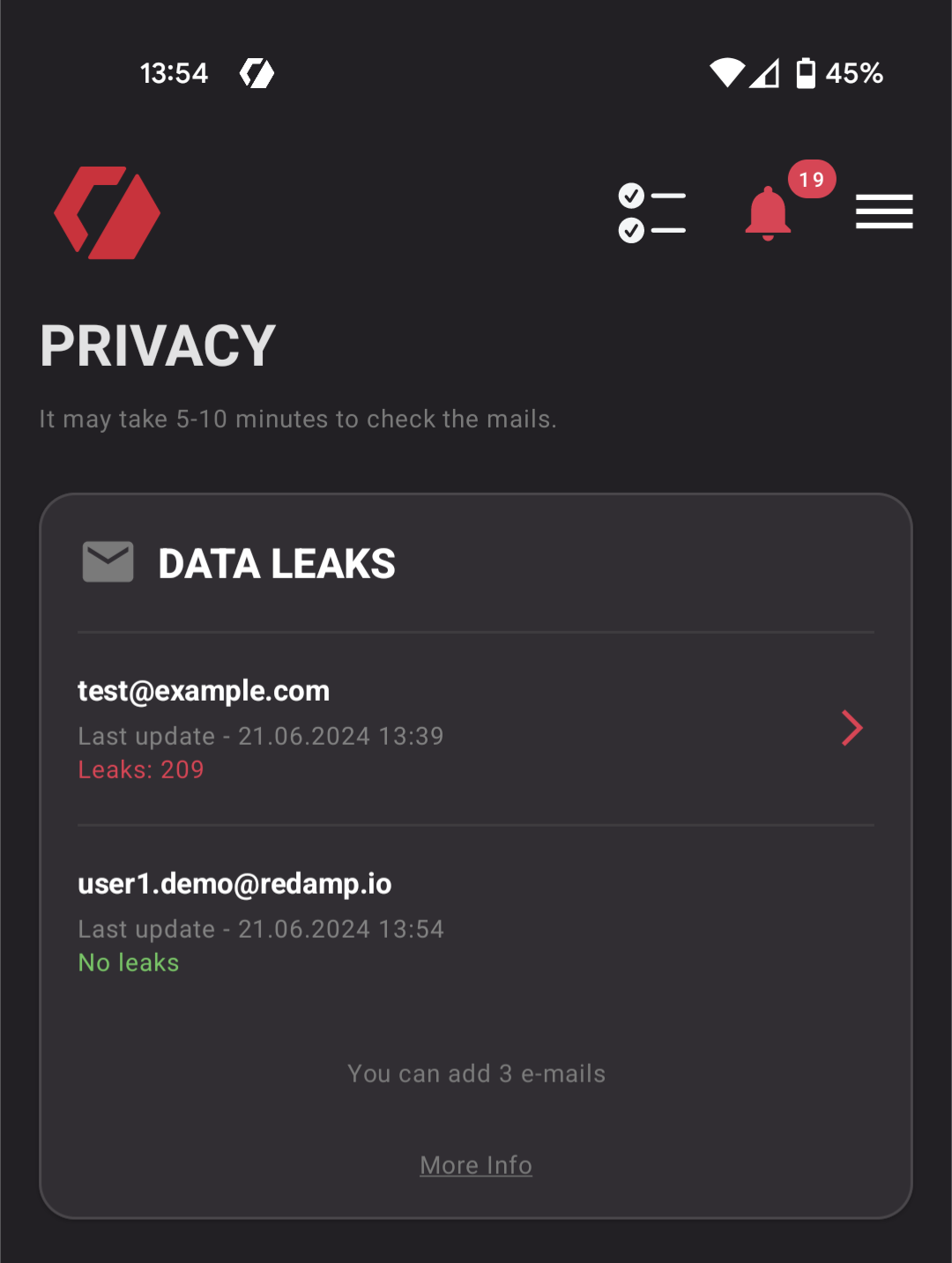
Notable Big Data Leaks
Warning: The following examples illustrate the severe consequences of data breaches involving email addresses. They highlight the importance of robust email security.
- Yahoo (2013-2014): One of the largest data breaches in history, affecting all three billion Yahoo accounts. Hackers stole names, email addresses, phone numbers, and security questions.
- Equifax (2017): This breach exposed personal information of 147 million people, including Social Security numbers, birth dates, and email addresses, which could be used for identity theft and financial fraud.
- Marriott International (2018): Information of approximately 500 million guests was compromised, including passport numbers, travel details, and email addresses.
- Facebook (2019): Data from 540 million users was exposed on an unsecured server, including email addresses and user activities, potentially leading to targeted phishing attacks.
- LinkedIn (2021): Data scraped from 700 million users was found for sale on a hacker forum, including email addresses and professional profiles, which could be used for social engineering attacks.