Device scan analysis
Guide on how to view and analyze device scan results on the Redamp.io console and mobile device.
You can view the results of your device scan on the Redamp.io console or on your mobile device. On your mobile device, you can only see the latest scan results with a basic evaluation. For more detailed information, you need to use the Redamp.io console.
Every scan result is divided into four categories:
- Device - Security evaluation of your
Mobile platform(Operating system, device model, etc.) andOS settings(Root status, screen lock, etc.) - Network - Security evaluation of the network
Settings(WPA2/3, DNS, VPN, etc.) andTraffic security(Traffic filtering, firewall, etc.) - Privacy - List of data breaches connected to
Email addressesyou've added - Apps - Security evaluation of the
Appsyou've on your device or added by yourself
Top section
Top panel

On the left side of the top panel, you can see the device vendor and model name (OnePlus - vendor, Nord - model name).
On the right side of the top panel, you can see the date and time of the last scan and these buttons:
- Calendar: Date picker for selecting a date of the scan you want to view
- Send notification: Send a notification to the device, either for a scan request or with a custom message. Please note that a scan request does not guarantee immediate scanning; it may not occur if the device is turned off, not connected to the internet, or for other reasons.
- Device settings: Option to archive the device if it's not in use anymore.
Device info
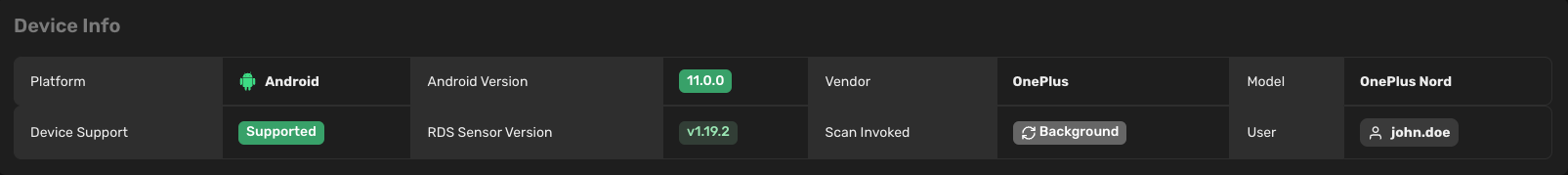
Basic information about your device, system, and user.
- Platform: Specifies the operating system of the device (Android, iOS, iPadOS, Windows, macOS, Linux)
- Platform version: Specifies the version of the operating system. If the tag is red, it means that the operating system is no longer receiving security updates.
- Vendor: Specifies the vendor of the device (Samsung, OnePlus, Apple, etc.)
- Model: Specifies the model name of the device (Galaxy S20, iPhone 12, etc.)
- Device support: Specifies the support status of the device. If the tag is red, it means that the device is no longer receiving security updates.
- Redamp.io version: Specifies the version of the Redamp.io app installed on the device. If the tag is red, it means that the mobile app is not updated to the latest version.
- Scan invoked: Indicates whether the scan was invoked by the user or automatically in the background by the Redamp.io mobile app.
- User: Specifies the user of the device.
Score panel

The score panel shows the overall score of the device in each category.
Overview tab
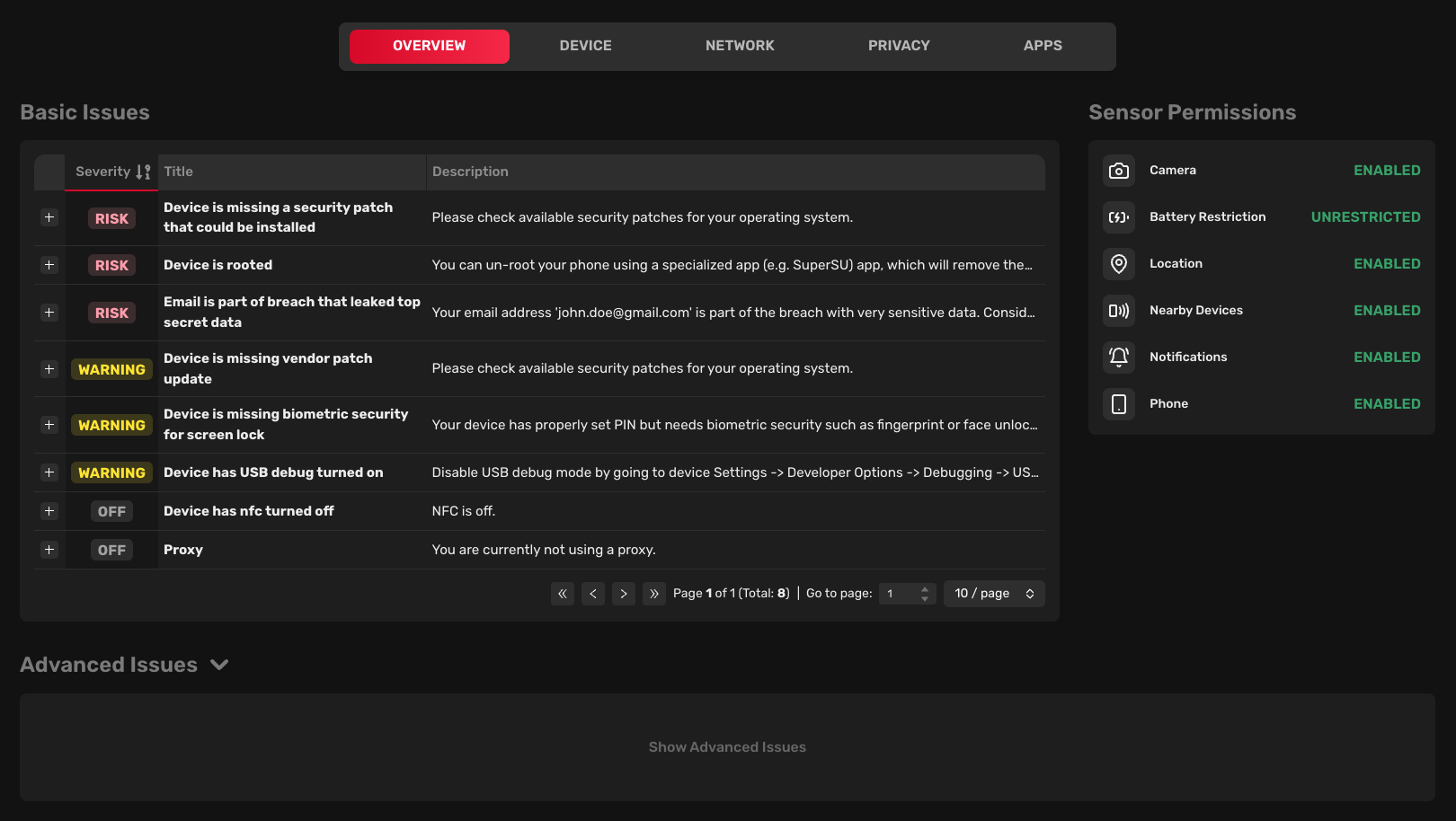
Basic issues
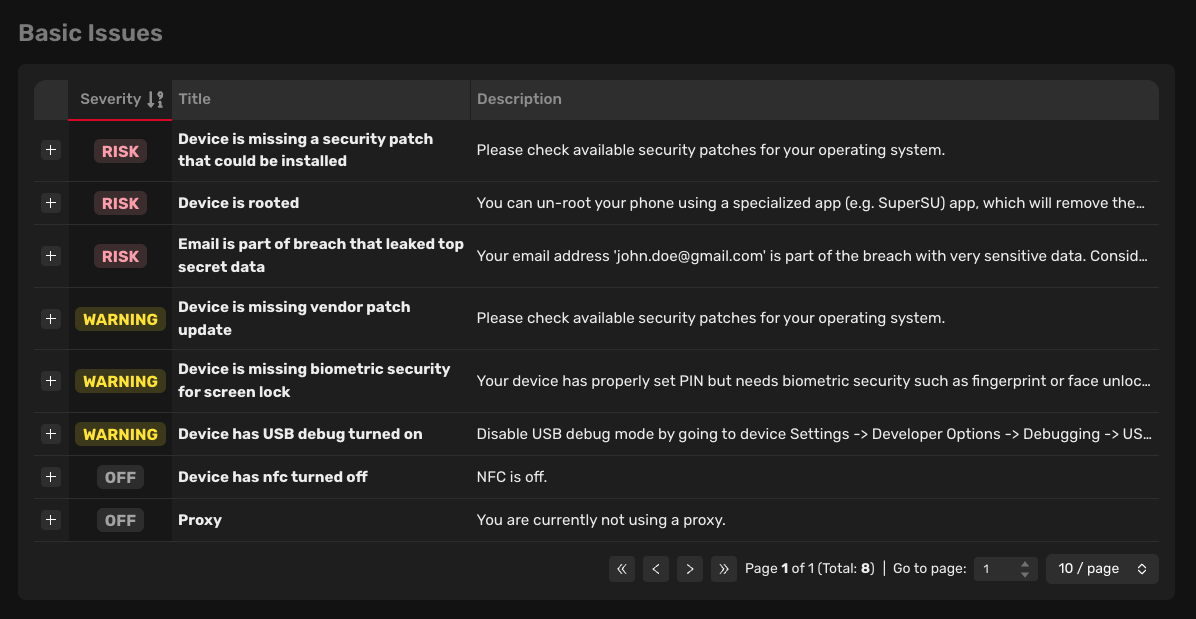
Each issue is assigned a severity (Low, Medium, or High), a number of affected devices, a title, and a description.
Clicking on the "plus" icon at the beginning of every row allows you to access more details about the issue. In the details, you can see a list of affected devices, a detailed description, a list of affected platforms, and a suggested solution for resolving the issue.
Sensor permissions
Sensor permissions show the status of the permissions required by the Redamp.io mobile app to perform a scan. If some permissions are not granted, we won't be able to perform a comprehensive scan of the device.
Android
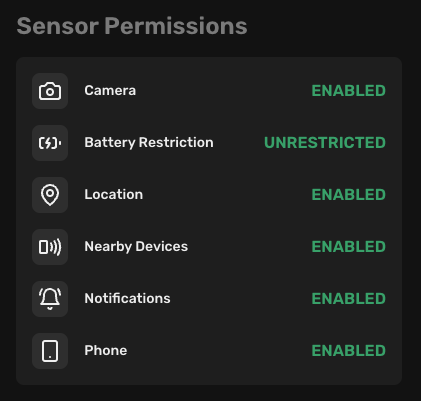
- Camera: We need camera access for scanning the pairing QR code during the onboarding process. - Enabled (Preferred): We have access to the camera. - Disabled: We don't have access to the camera.
- Battery restriction: We need to disable battery optimization for the Redamp.io mobile app to perform a background scan. - Unrestricted (Preferred): Our app is not restricted in performing background scans. - Optimized: The background scan won't always work. - Restricted: We cannot perform a background scan.
- Location: We need location access for gathering detailed information about network security. - Enabled (Preferred): We can gather detailed information about network security. - Disabled: We cannot gather detailed information about network security.
- Nearby devices: We need nearby devices access for gathering detailed information about other devices on the network. - Enabled (Preferred): We can gather detailed information about other devices on the network. - Disabled: We cannot gather detailed information about other devices on the network.
- Notifications: We need notification access for sending notifications to the device. - Enabled (Preferred): We can send notifications to the device. - Disabled: We cannot send notifications to the device.
- Phone: We need phone access for gathering detailed information about the device. - Enabled (Preferred): We can gather detailed information about the device. - Disabled: We cannot gather detailed information about the device.
iOS
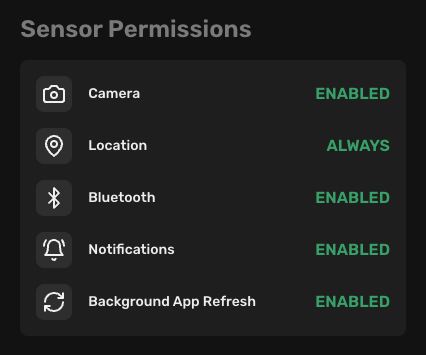
- Camera: We need camera access for scanning the pairing QR code during the onboarding process. - Enabled (Preferred): We have access to the camera. - Disabled: We don't have access to the camera.
- Location: We need location access for gathering detailed information about network security. - Enabled (Preferred): We can gather detailed information about network security. - Disabled: We cannot gather detailed information about network security.
- Bluetooth: We need Bluetooth access for gathering information about the Bluetooth status. - Enabled (Preferred): We can gather information about the Bluetooth status. - Disabled: We cannot gather information about the Bluetooth status.
- Notifications: We need notification access for sending notifications to the device. - Enabled (Preferred): We can send notifications to the device. - Disabled: We cannot send notifications to the device.
- Background app refresh: We need background app refresh access for performing a background scan. - Enabled (Preferred): We can perform a background scan. - Disabled: We cannot perform a background scan.
Advanced issues
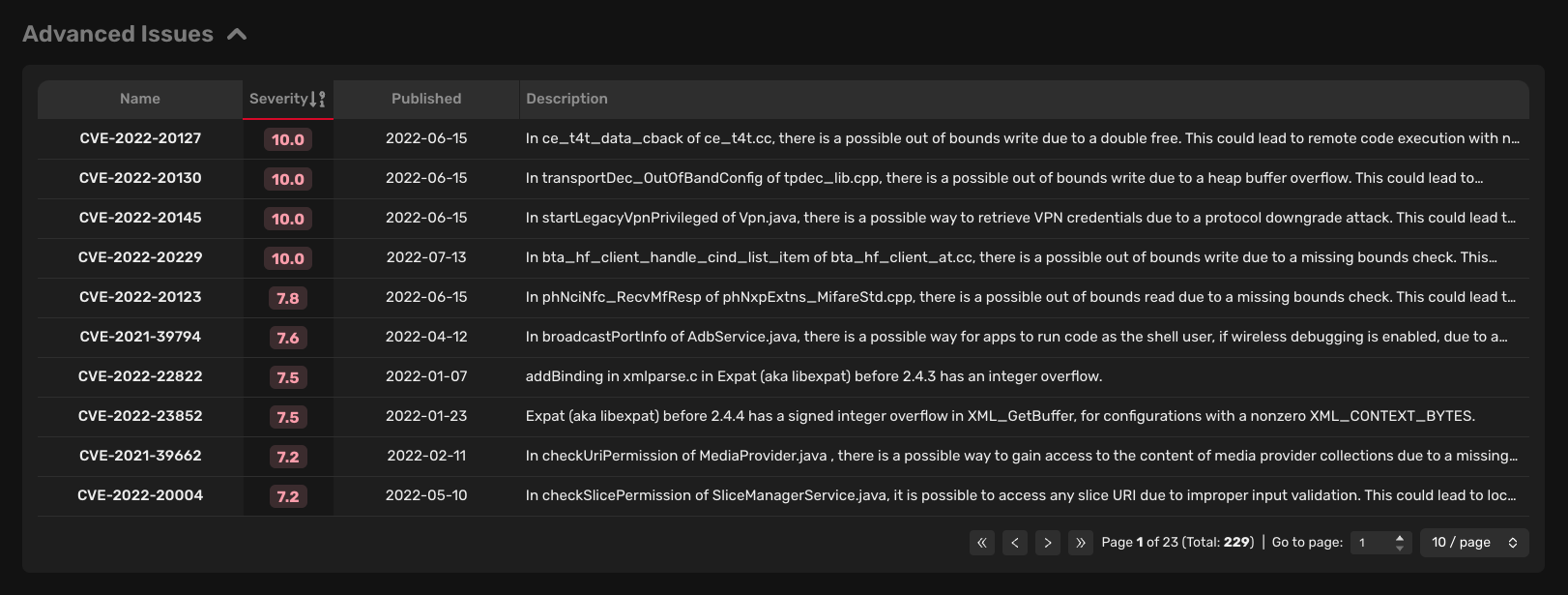
Advanced issues include CVEs (Common Vulnerabilities and Exposures) that have been assigned a CVE ID. CVEs are publicly known vulnerabilities assigned by the CVE Numbering Authority (CNA) to uniquely identify a specific vulnerability or exposure. These vulnerabilities or exposures are assigned a severity score (CVSS score) to determine their severity.
Each advanced issue is assigned a CVE ID, a severity score (based on the CVSS score), a publish date, and a CVE description.
Device tab
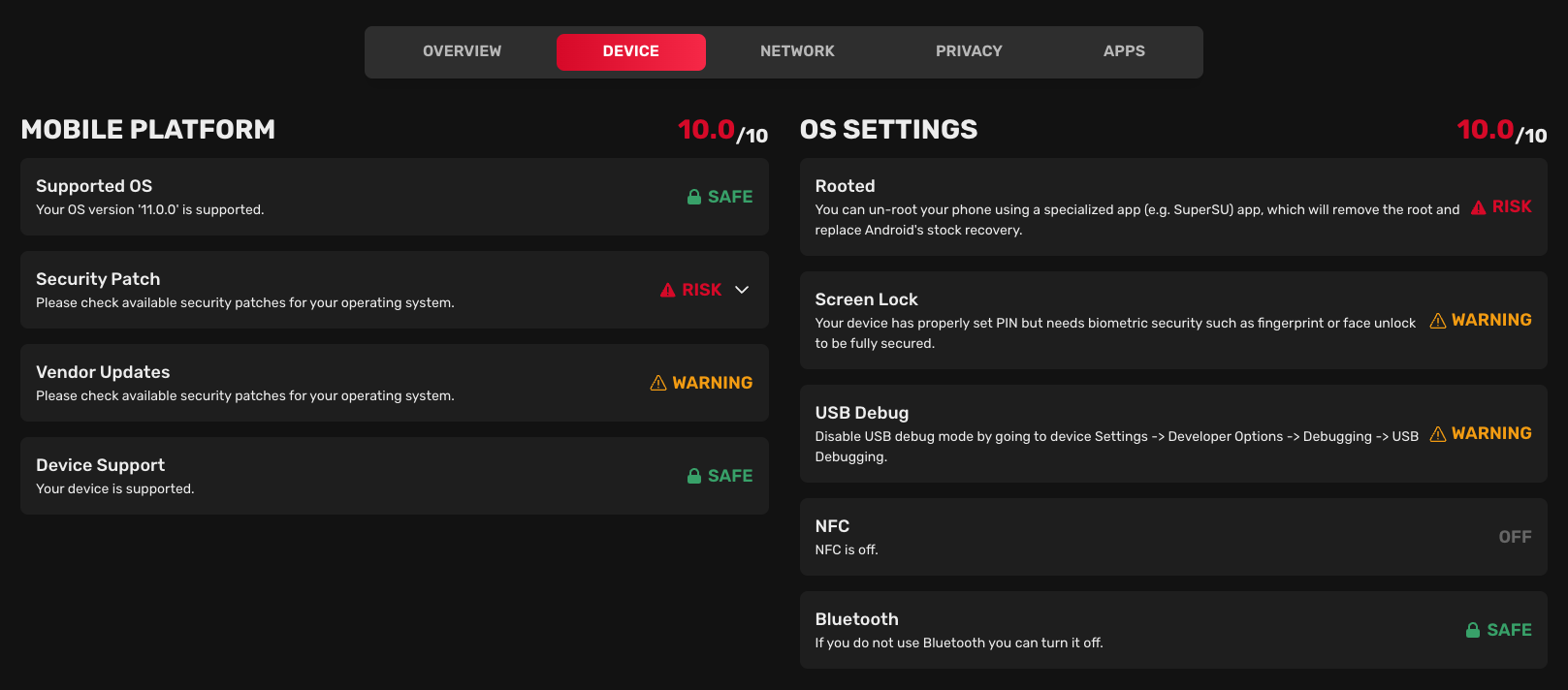
Mobile platform
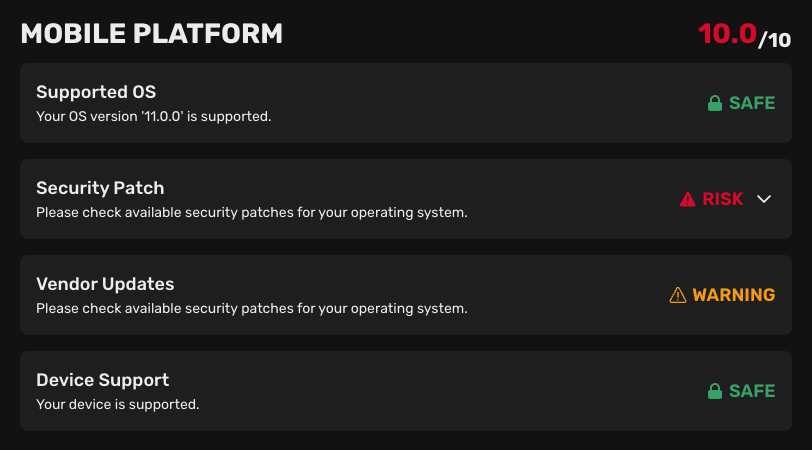
The mobile platform section describes the security status of the operating system version:
- Supported OS: Indicates whether the operating system version is supported by the manufacturer.
- Security patch: Indicates whether the operating system version has the latest security patch.
- Vendor updates (Android only): Indicates whether the device is missing security updates from the manufacturer.
- Device support: Indicates whether the device is going to receive security updates from the manufacturer.
OS settings
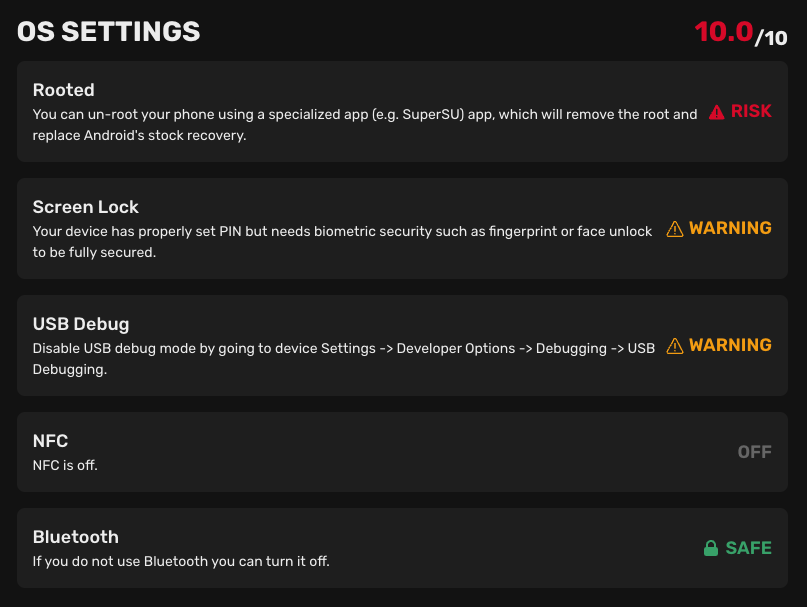
The OS settings section describes the security status of the operating system settings:
- Rooted/Jailbroken: Indicates whether the device is rooted/jailbroken.
- Screen lock: Indicates what type of screen lock is used on the device. - Android: - Biometrics (Recommended): Secured by FaceID or Fingerprint. - PIN: Secured by PIN Code. - None: Device is without any screen lock. - iOS: - FaceID (Recommended): Secured by scanning your face. - TouchID: Secured by scanning your fingerprint. - PIN: Secured by entering a passcode. - None: Device is without any screen lock.
- USB debug (Android only): Indicates whether USB debugging is enabled on the device.
- NFC: Indicates whether NFC is turned on/off on the device.
- Bluetooth: Indicates whether Bluetooth is turned on/off on the device.
Network tab
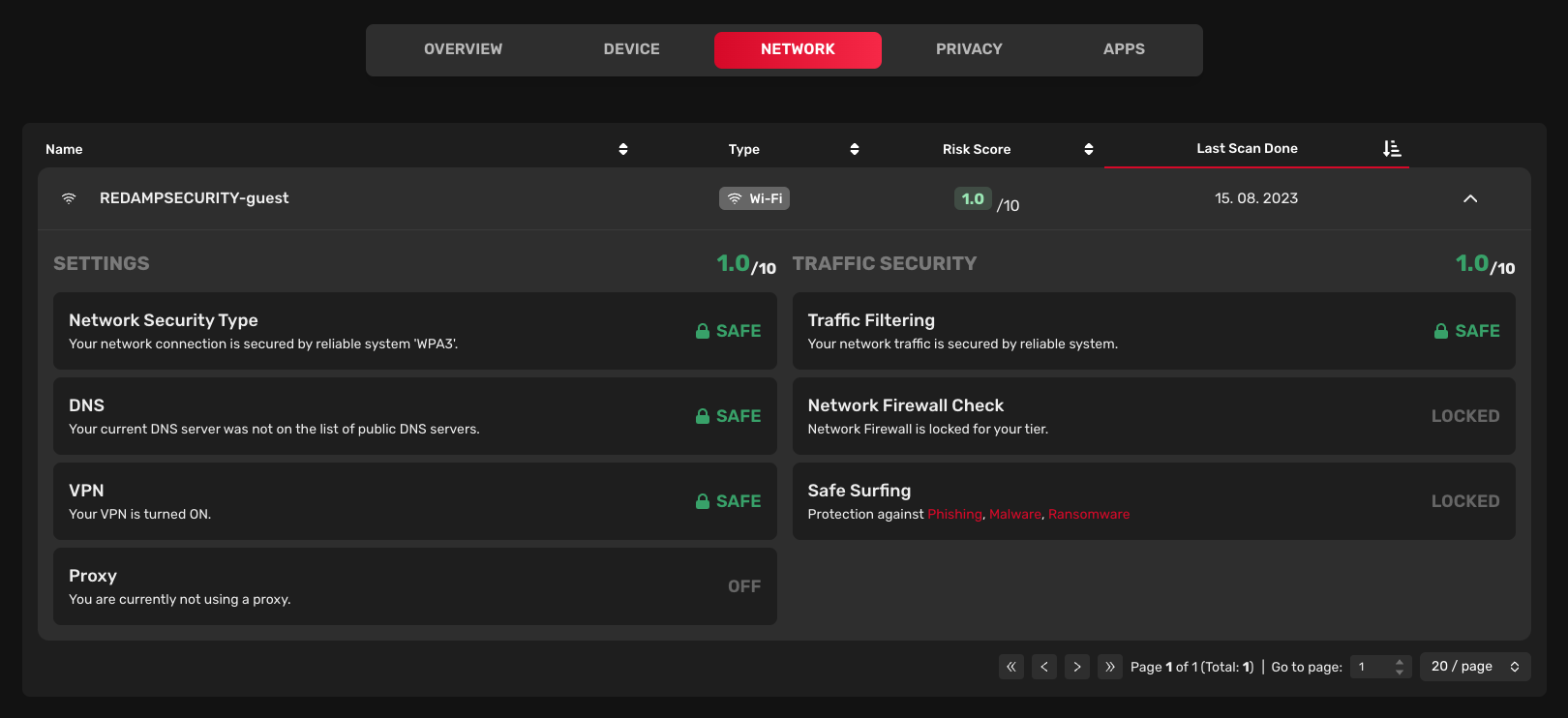
The Network tab displays a list of networks scanned by the device. You can view a brief security summary for each network.
Settings
- Network security type: Indicates the encryption type of the wireless network (e.g. WPA2, WPA3, etc.).
- DNS: Indicates whether the DNS is publicly known or not.
- VPN: Indicates whether VPN is turned on/off on the device.
- Proxy: Indicates whether Proxy is turned on/off on the device.
Traffic security
- Traffic filtering: Indicates whether the network uses some type of traffic filtering.
- Network firewall check: Indicates whether the network uses a firewall. Locked in the current version.
- Safe Surfing: Indicates whether the device has safe surfing turned on. Locked in the current version.
Privacy tab
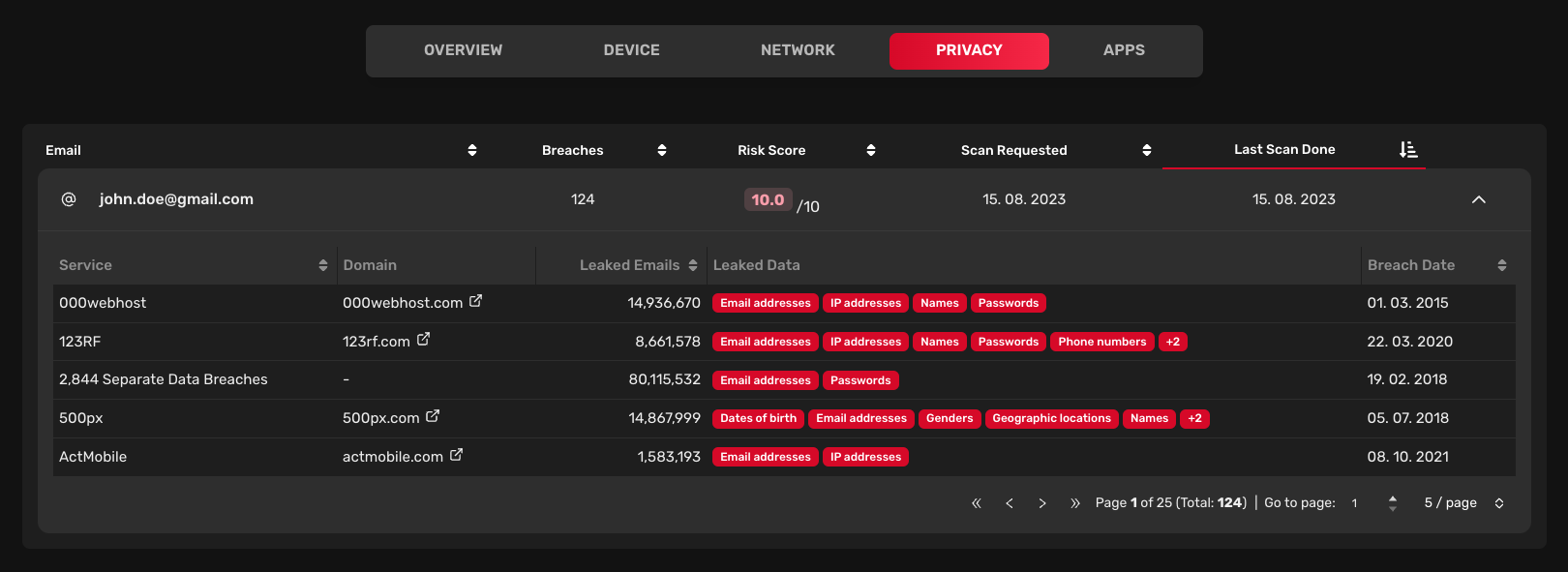
The Privacy tab displays a list of scanned email addresses for data breaches.
After clicking on the email address, you can view a data breach summary for each email address. Each data breach includes:
- Service: Name of the service where the data breach occurred.
- Domain: Domain of the service where the data breach occurred.
- Leaked emails: Number of leaked emails.
- Leaked data: Type of leaked data.
- Breach date: Date when the data breach happened.
Apps tab
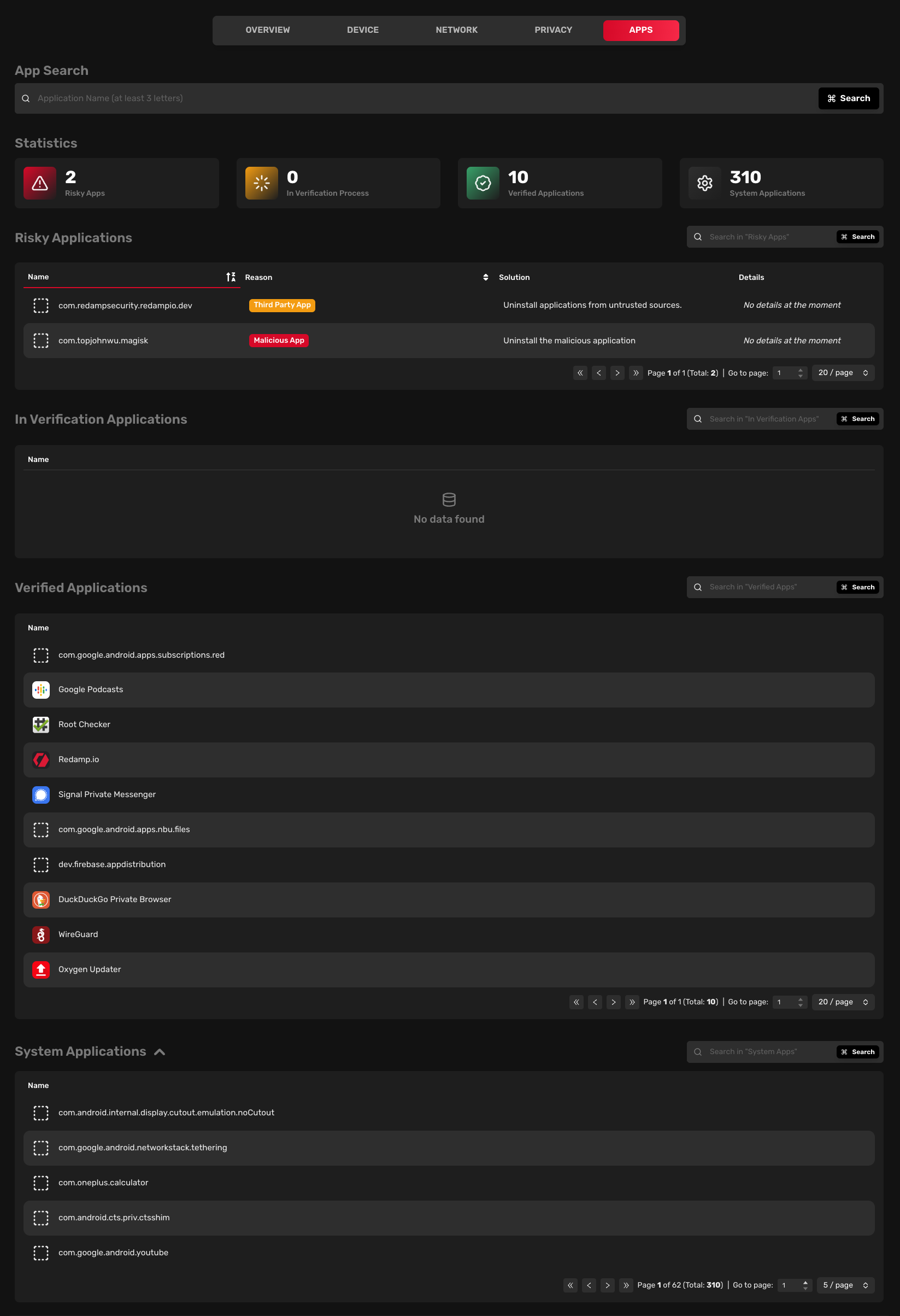
The Apps tab displays a list of installed apps on the device. You can view a brief security summary for each app.
Risky applications
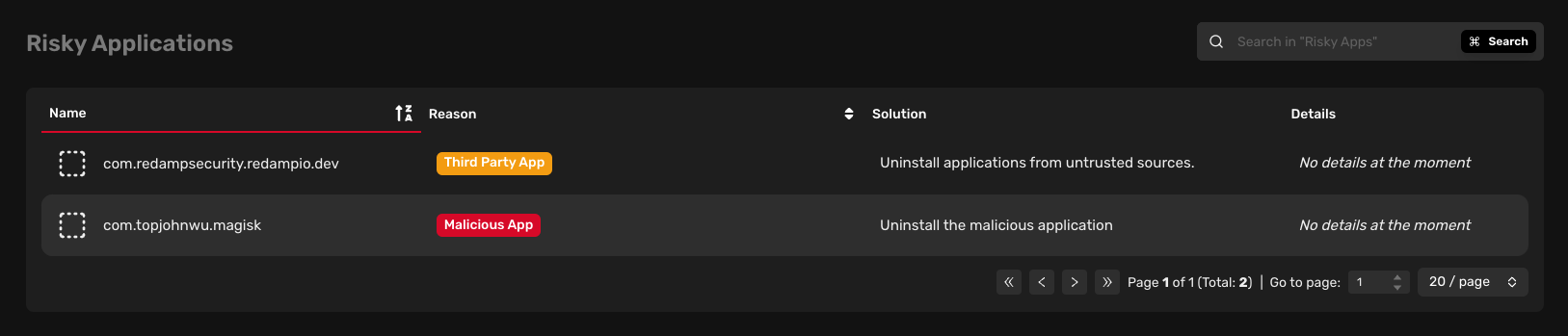
Risky apps are known to be malicious, are no longer maintained, or were not installed from an official app store. We recommend keeping an eye on these apps and considering uninstalling them.
In verification applications

In verification apps are apps that are not yet verified by our team. Analysis of these apps is in progress and they will be moved either to the "risky" category or to the "verified" category.
Verified applications
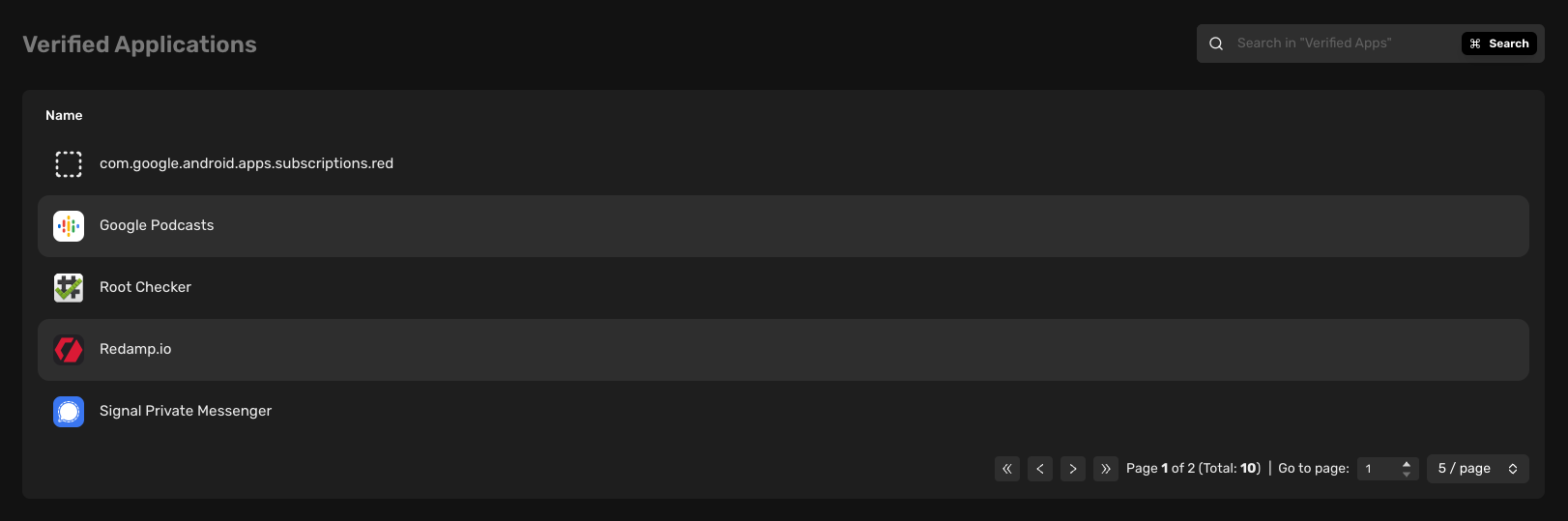
Verified apps are apps that are installed from the official app store and our analysis team did not find any security issues with them.
System applications
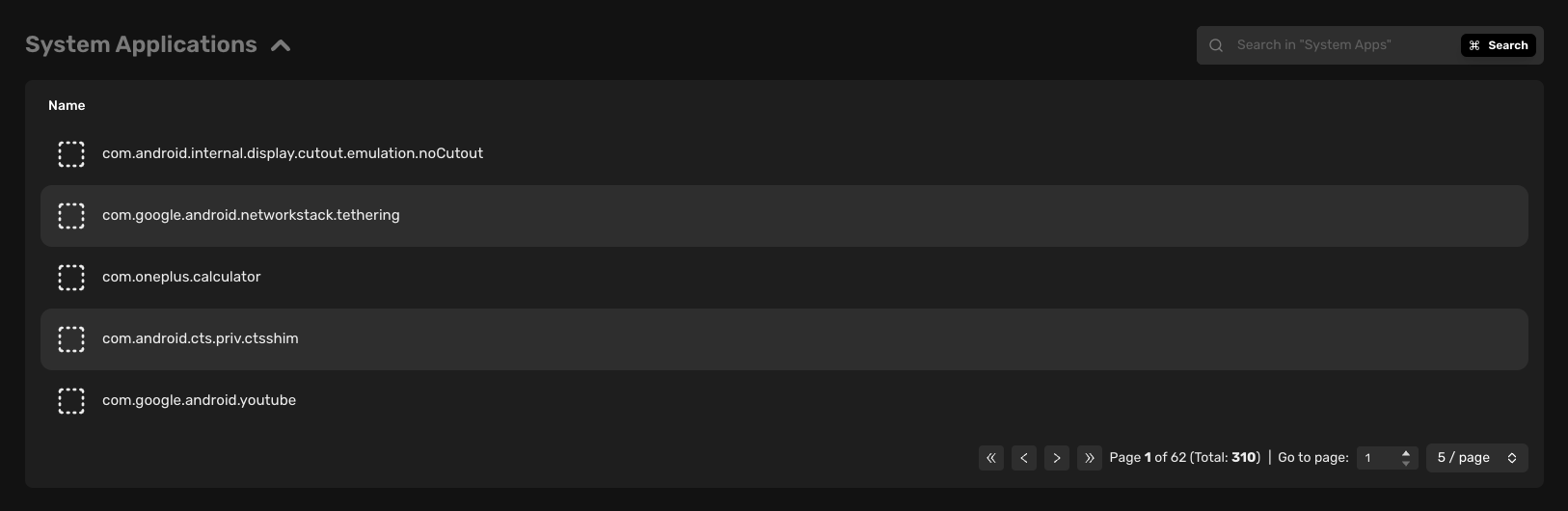
System apps are apps that are installed by the manufacturer and are part of the operating system.