Corrupted Word Files As a New Phishing Tactic
According to experts, cybercriminals have discovered an innovative tactic to evade online defenses and deliver phishing emails straight to your inbox.

A new phishing technique exploits Microsoft's Word file recovery feature by sending intentionally corrupted Word documents as email attachments. These files evade security software by appearing damaged but remain recoverable within the Word application.
Cybercriminals are continually innovating to bypass email security measures and ensure their phishing emails reach victims' inboxes.
The latest campaign, uncovered by the malware analysis company ANY.RUN , uses this method with emails impersonating payroll and human resources departments, tricking recipients into engaging with the malicious attachments.
What does scam look like in practice?
-
A user receives an email that appears to be from company's HR department. The subject of the email is financial rewards or the payment of a bonus at the end of the year.
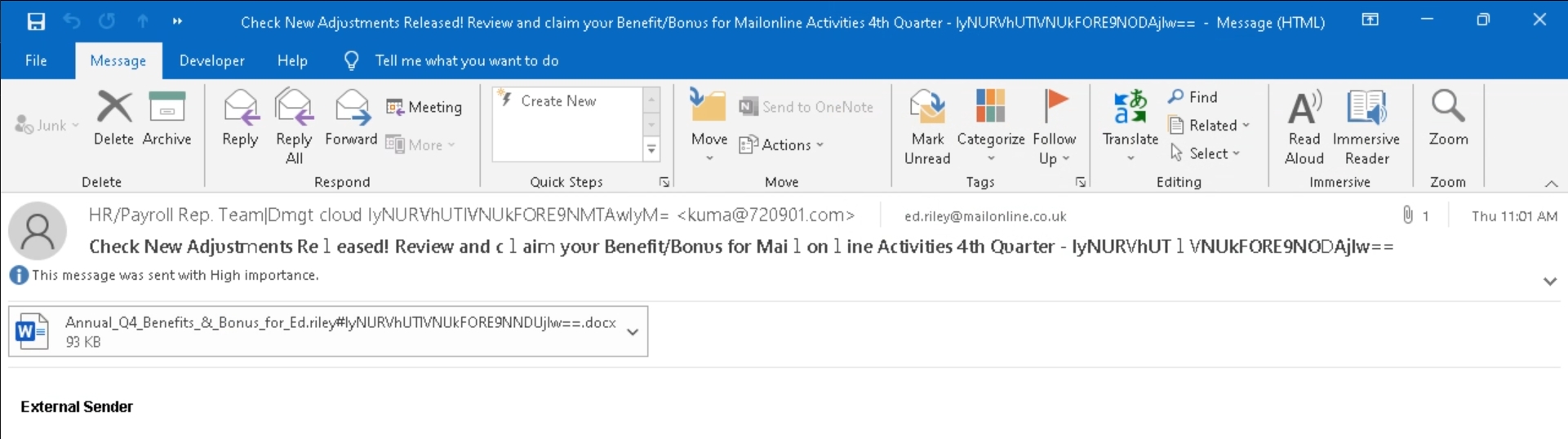
-
The email contains an attachment that pretends to be a legitimate Microsoft Word document. Examples of possible names:
Annual_Benefits_&_Bonus_for_[name].docxAnnual_Q4_Benefits_&_Bonus_for_[name].docx.binBenefits_&_Bonus_for_[name].docx.binDue_&_Payment_for_[name].docx.binQ4_Benefits_&_Bonus_for_[name].docx.bin
-
The user downloads the supposed document to their computer and attempts to open it.
-
However, the document is intentionally corrupted by attackers and the user is presented with the following warning.
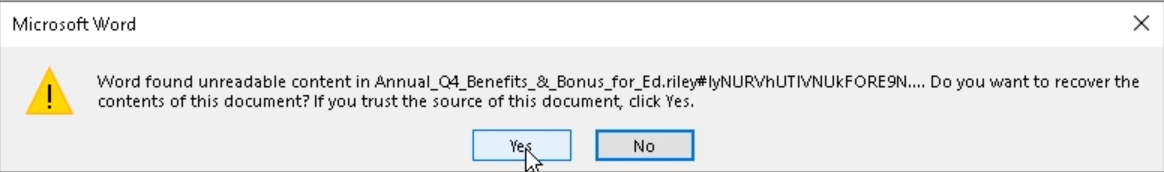
-
If the user decides to click
Yesand recover the document, Microsoft Word will automatically repair the corrupted file. -
Normally, your antivirus program would probably report that you have opened a potentially malicious file by now. However, in this case, because the file is corrupted, standard analysis cannot be performed.
-
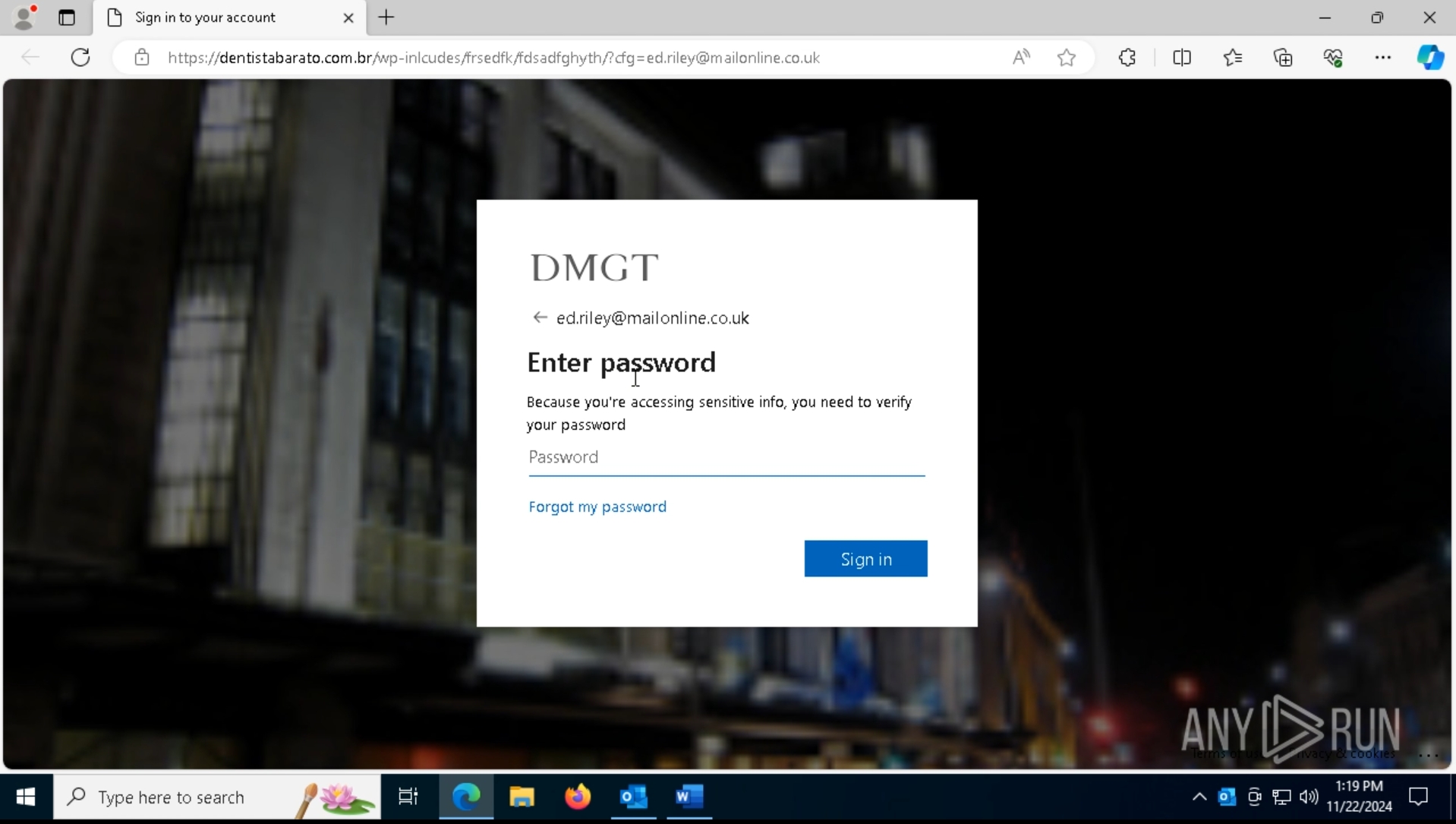
The repaired document contains a QR code:

-
Scanning the code will redirect you to a phishing page. In this case, attackers imitate the login to Microsoft 365 services. Entering your login details into the form will compromise your account and, if it is an employee's corporate account, very sensitive internal data may be stolen.
How to defend yourself?
Even though attackers use new techniques, the essence of a phishing attack is still the same: tricking a user into unknowingly landing on a fraudulent page and filling out their login or financial details.
- Our app Redamp.io includes a Safe Surfing feature that effectively handles protection against the latest threats such as phishing or malware.
- Be cautious when you receive a message from an unknown sender.
- Think twice about downloading and opening attachments that look suspicious, especially if they appear to contain sensitive information, such as your company's financial results or employee compensation reports. In many cases, these are simply bait from attackers.
- Check the links in the body of the email and do not click on them if they look unfamiliar or suspicious.
- Do not try to scan unknown QR codes with your mobile phone.
- Continuously educate yourself. in the field of cybersecurity to be able to respond to the latest tactics of attackers.