Phishing Campaigns Abusing User Information in Links
Cybercriminals have revived an overlooked feature of web URLs — the @ symbol, commonly associated with email addresses — and are now exploiting it to mask links to their malicious websites.

Good Old Phishing Tricks with @ Sign
A recent phishing method employs URLs that feature legitimate-looking domain names followed by the @ symbol, such as [email protected]. At first glance, this URL appears linked to a trusted site google.com. However, the actual destination of the link is redamp.io, not the domain it seems to reference.
The most recent case was captured by the Internet Storm Center . In the image below you can see a phishing email that contains a very long link starting with https://facebook.com
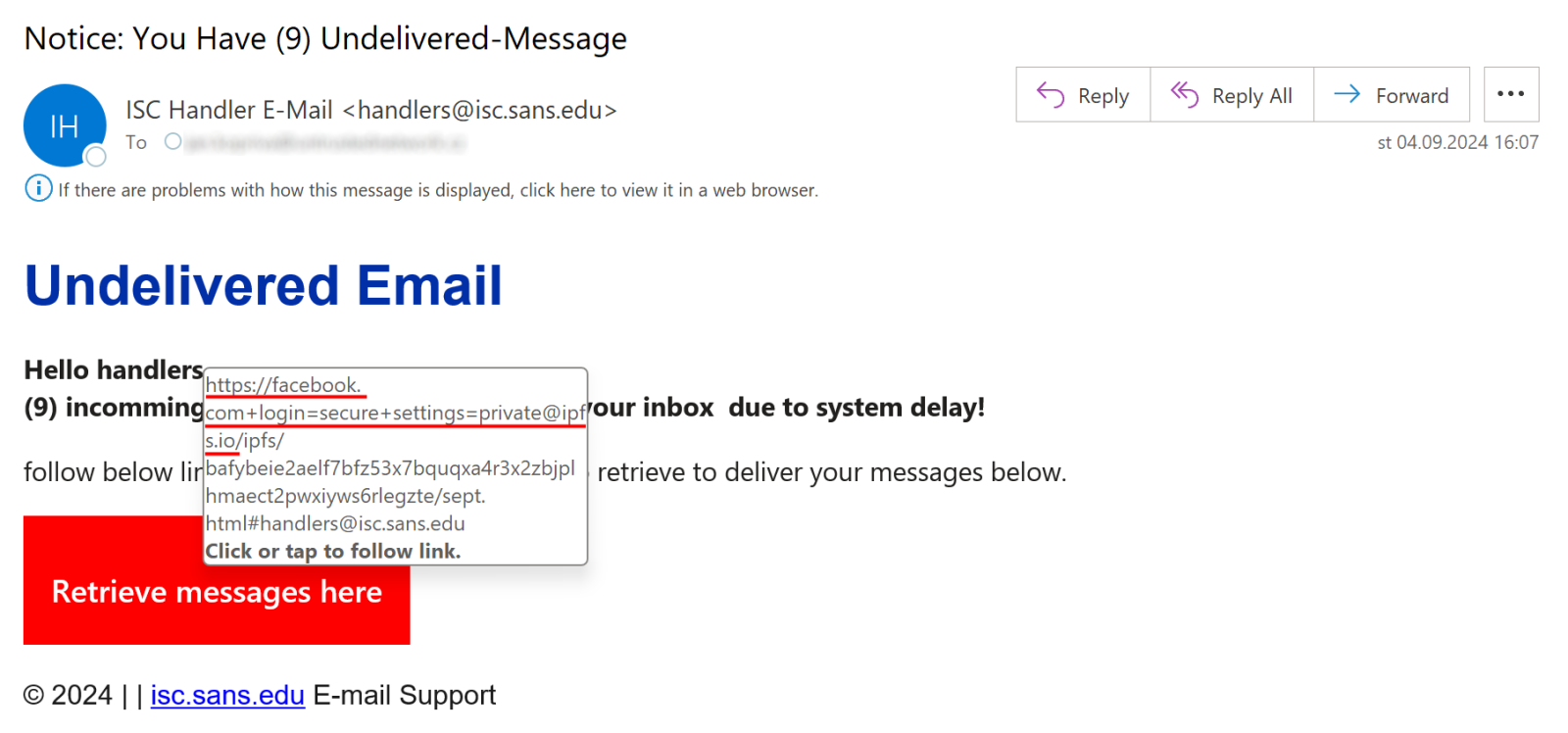
This is followed by other words such as login, secure, settings and private to give the impression that this is a legitimate link.
The entire link may seem nonsensical and dysfunctional at first glance, but the attackers know exactly what they are doing. The link in the body of the email is precisely crafted to be valid and can be opened by most web browsers without further warning or user interaction.
If people are already at least a little bit educated and check internet links, they usually start reading them from the left and move on to the right. If they come across legitimate-looking words, they often stop checking and click on the link. Attackers are aware of this and try to make the link look as authentic as possible.
As Malwarebytes points out in their article, links can also come out very complicated and unreadable. For example:
https://$%^&;****((@bit.ly/3vzLjtz#ZmluYW5jZUBuZ3BjYXAuY29t
This kind of masking is intended to confuse users who honestly check the links in the bodies of incoming emails. The user may evaluate the jumble of characters and symbols as something they don't need to check because it looks at first glance like part of computer source code and therefore nothing of interest to the average user.
Another example shows that fraudulent links of the same type can also be found on social networks. Here, the attackers have not gone to the trouble of disguising themselves, but an untrained user may not be able to tell the difference from a normal link.

How To Stay Safe?
What can you do to protect yourself most effectively against this type of fraud?
-
Our mobile app Redamp.io includes a Safe Surfing feature that effectively handles protection against the latest threats such as phishing or malware.
-
Examine links thoroughly: Rather than just hovering over them, take the precaution of manually typing URLs directly into your browser.
-
Avoid clicking on any links that seem suspicious or come from unsolicited emails.
-
Exercise caution with URLs containing
@symbols: If you come across a URL featuring an@, particularly when followed by a well-known domain name, proceed with care. Such URLs are frequently employed in phishing schemes. -
Follow the recommendations on our page describing other types of phishing.