Phishing Links Hidden from Outlook Users
Cybersecurity experts have uncovered a sophisticated phishing technique that exploits special modifications in email source code to make a message appear differently in Microsoft Outlook than on other platforms.

Tricky and Sophisticated Phishing
Cybercriminals use this technique to hide harmful links from corporate security systems while ensuring that victims accessing the email via non-Microsoft Outlook platforms are redirected to phishing websites.
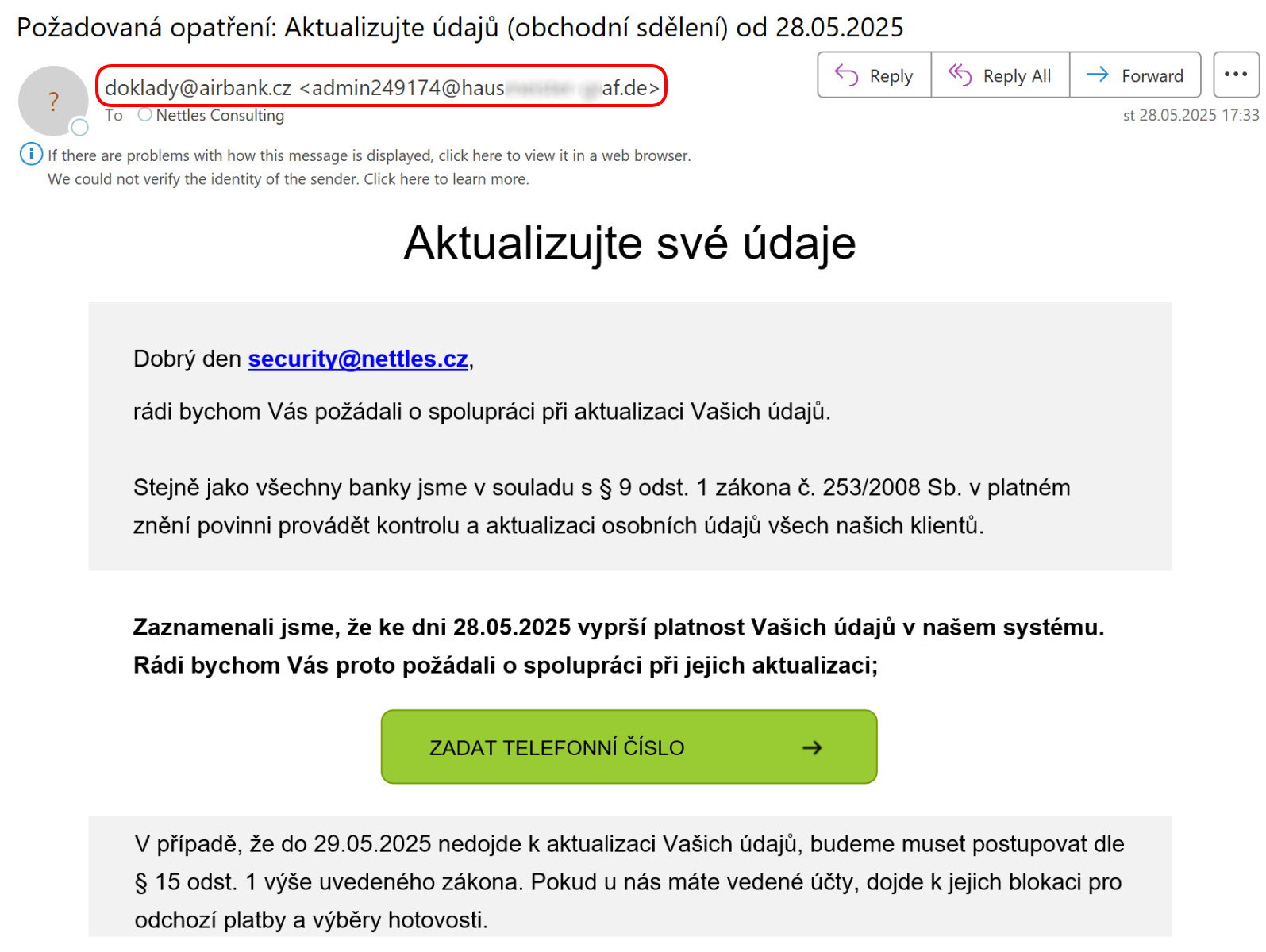
The phishing email shown below posed as an official message from a leading Czech bank, urging account holders to update their personal details through a provided link.
The first thing the user should notice is the suspicious-looking email address of the sender (marked in red):
Upon closer inspection, investigators noticed an unusual detail: hovering over the call-to-action button showed that the embedded link directed users to the bank’s official domain.
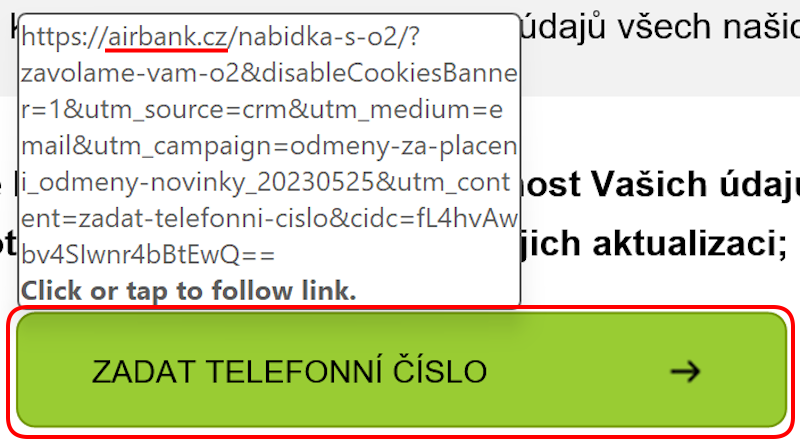
At first, it seemed like the attackers had made a significant error—sending out a phishing template before swapping legitimate URLs for malicious ones.
While such mistakes are rare, they have been observed in past cybercriminal campaigns. However, a deeper examination of the email’s HTML source code uncovered a highly sophisticated attack strategy, showcasing advanced technical expertise and meticulous planning.
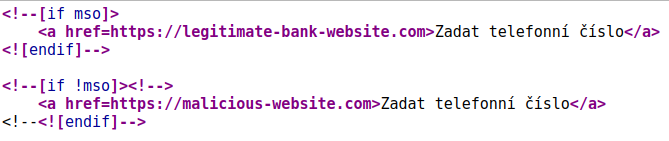
This phishing campaign exploits HTML conditional comments, which were initially intended to maintain uniform email formatting across various email clients. An example of source code with both conditions can be found below:
HTML (HyperText Markup Language) is the standard language used to structure and display content on the web.
When viewed in Microsoft Outlook, the email displays a hyperlink leading to the official banking website, giving it a harmless appearance that can easily bypass most automated security checks.
In contrast, when the email is opened in other email clients like Gmail, Apple Mail, or web browsers, the conditional logic triggers a malicious redirect, sending users to fraudulent sites designed to capture banking credentials and personal data.
How to Stay Safe?
Although this is an advanced way to trick users, it is still possible to mitigate the risk by following the basic rules of phishing defense:
- Use Safe Surfing feature in our Redamp.io application that can filter out malicious URLs.
- Always examine the sender's email address before taking any action. Pay attention to small variations or misspellings in the email address, as cybercriminals often use similar-looking addresses to trick recipients.
- Be cautious when encountering links or attachments in emails, especially from unknown sources. Phishers often use enticing language to manipulate recipients into clicking on malicious links or downloading harmful attachments.
- Strengthen your account security by enabling multi-factor authentication (MFA/2FA) wherever possible. MFA requires an additional verification step beyond your password, making it significantly more challenging for unauthorized individuals to access your accounts.
- Stay informed! Read our blog and follow notifications in the Redamp.io app about the latest threats we are monitoring for you.
Sources:


