Don't Fall for It! The Top Tricks of Scammers
The internet makes life easier—shopping, chatting, banking, or working from home. But alongside all this convenience, there are serious dangers that most people aren’t aware of. You don’t need to be a computer expert to stay safe—you just need to know what threats exist and how to avoid them.

📨 Phishing – Tricking You with Fake Emails
Phishing happens when criminals send emails or texts pretending to be someone you trust (like your bank or a delivery company) to steal your personal information.
What to look for:
- Urgent messages asking you to act quickly.
- Links that don’t match the real company website.
- Unusual sender addresses or poor grammar.
Examples:
- Cybercriminals are distributing convincing fake emails that mimic Apple Support , falsely notifying recipients that their Apple IDs have been suspended.
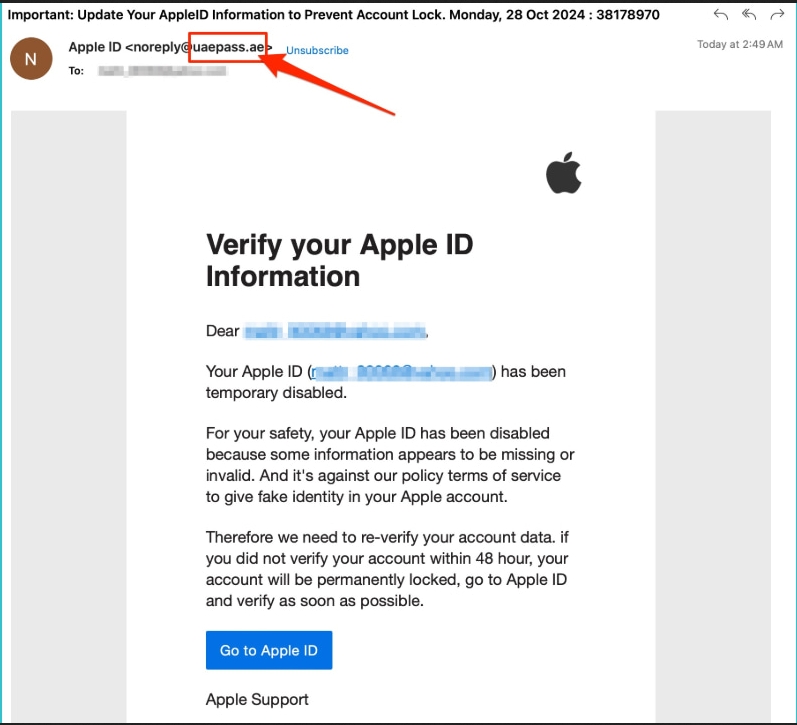
- Unsubscribe Email Scam : Cybercriminals send fake emails with a link to unsubscribe from advertising campaigns to get users to click on it.
- A phishing technique exploits Microsoft's Word file recovery feature by sending intentionally corrupted Word documents as email attachments . These files evade security software by appearing damaged but remain recoverable within the Word application.
- CEO Fraud is a form of cybercrime in which attackers pose as a company's top executives to deceive employees into making unauthorized money transfers or revealing confidential information.
📞 Vishing – Scam Calls That Trick You
Vishing stands for “voice phishing.” Criminals call you pretending to be from your bank, internet provider, or even the police. They try to scare or confuse you into giving away personal or financial information.
What to look for:
- Calls that create urgency or panic (e.g., "Your bank account is in danger!").
- Requests for personal info like PINs or passwords.
- Callers who won’t let you hang up and call back.
Tip: Banks and companies will never ask for sensitive information over the phone. Always hang up and call back using the official number from the company’s website.
Examples:
- Alleged Bank Fraud Alert: You might get a call saying there's unusual activity on your bank account. They’ll ask for your account details to “verify” your identity.
- Police or Government Threat : The caller claims you owe back taxes and will face legal trouble if you don’t pay immediately.
- Tech Support: Scammers call pretending to be from Microsoft, Apple, or another tech company, saying your computer has a virus. They convince you to let them access your device or to pay for unnecessary repairs.
- Investment offer: An unknown person calls with a very profitable online investment offer, trying to convince you to transfer funds to a bank account belonging to fraudsters.
- A phone call from a family member : Or you get a call from someone who claims to be a member of your family and needs your help with, for example, an unexpected expense in the budget.
🕷️ Malware – Hidden Programs That Harm Your Devices
Malware is harmful software that can infect your phone or computer if you click on a bad link or install something untrustworthy. It can steal your data, spy on your activity, or even lock your files.
What to look for:
- Pop-ups claiming your device is infected.
- Unfamiliar apps appearing after clicking links.
- Sudden slowdowns or strange behavior on your device.
Examples:
- Mandrake Android Spyware : A sophisticated spyware targeting Android devices. It has been linked to various cyber-espionage activities and is known for its extensive capabilities to monitor and control infected devices.
- Fake Google Ads Promote Malware Sites With Authenticator App : Cybercriminals use Google ads that link to fake sites promoting the malicious Google Authenticator app.
- Credit Card Data Being Stolen via NFC by NGate Android Malware : NGate allows attackers to clone victims' cards, enabling them to make unauthorized payments or withdraw cash from ATMs.
- Fake CAPTCHA scams : We’ve all encountered CAPTCHAs — those quick puzzles that confirm you’re a human and not a bot. However, cybercriminals have started using fake CAPTCHAs as a way to trick users into executing malicious commands on their systems.
💬 Scams on Social Media and Messaging Apps
Criminals send messages or post ads pretending to offer giveaways, job offers, or help from a friend. They try to steal your money or personal info.
What to look for:
- Messages asking for money out of the blue.
- Accounts with few friends, posts, or photos.
- Strange behavior from someone you “know.”
Also read: Social Networks Safety Tips
Examples:
-
Scams Offering Cheap Packages of Forgotten Goods : Scammers on Facebook are advertising cheap pallets and mystery boxes claiming to contain undelivered goods from major retailers like Amazon. These scams redirect you to fraudulent websites designed to steal your payment information.
-
Don’t Let Scammers Steal Your Facebook Login : Scammers have seized the opportunity to launch phishing campaigns, pretending to be official Meta representatives. These fake messages, often flooding replies to Marketplace listings or public posts, ask users to "verify" accounts or resolve fake issues, aiming to steal login information.
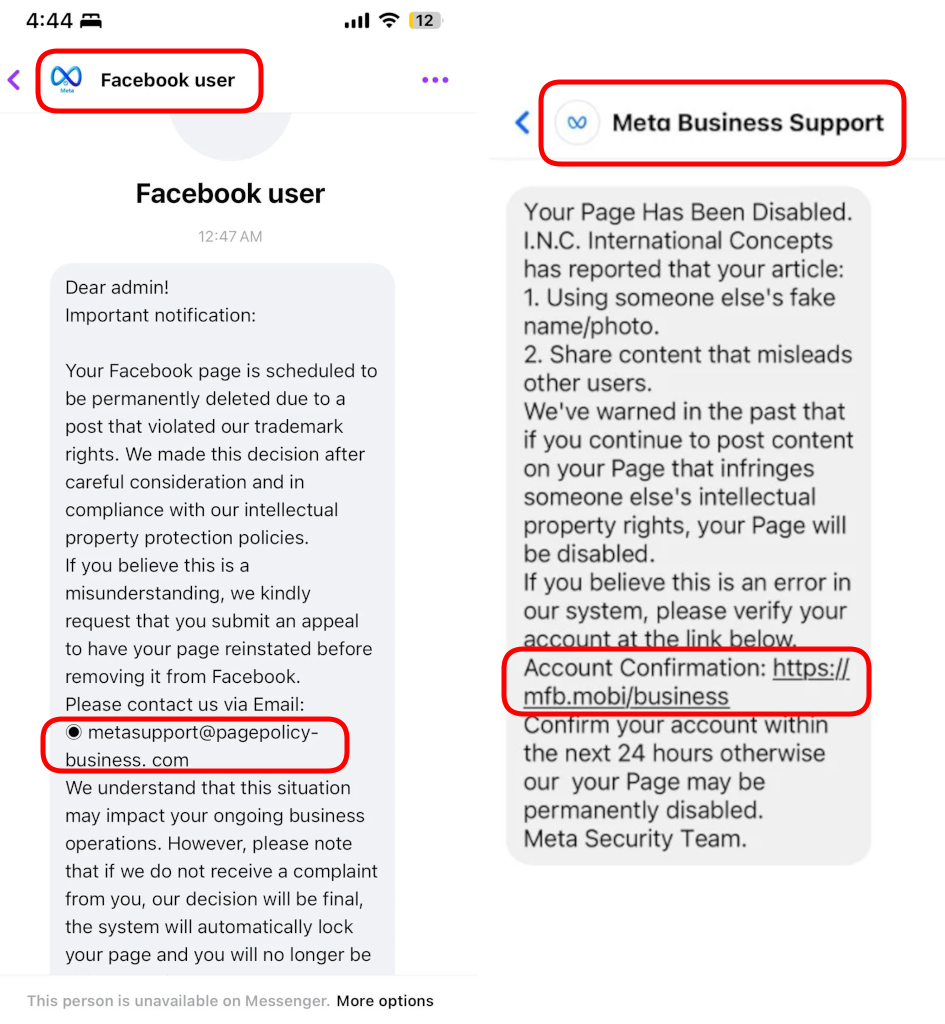
-
Famous Faces, Fake Posts: The Rise of Celebrity Facebook Scams : From fake giveaways to bogus investments, scammers are using celebrity identities to gain your trust—and your cash. These schemes are spreading fast on Facebook, catching even the most cautious users off guard.
🛒 Online Shopping Scams
Fake websites or social media ads sell items that never arrive, or they take your payment info and disappear.
What to look for:
- Prices that are much lower than usual.
- No real contact info or return policy.
- Bad grammar or suspicious web addresses.
Examples:
- Black Friday Scams : A trick used by scammers to steal your money, personal information, or even your identity during the busy shopping period around Black Friday.
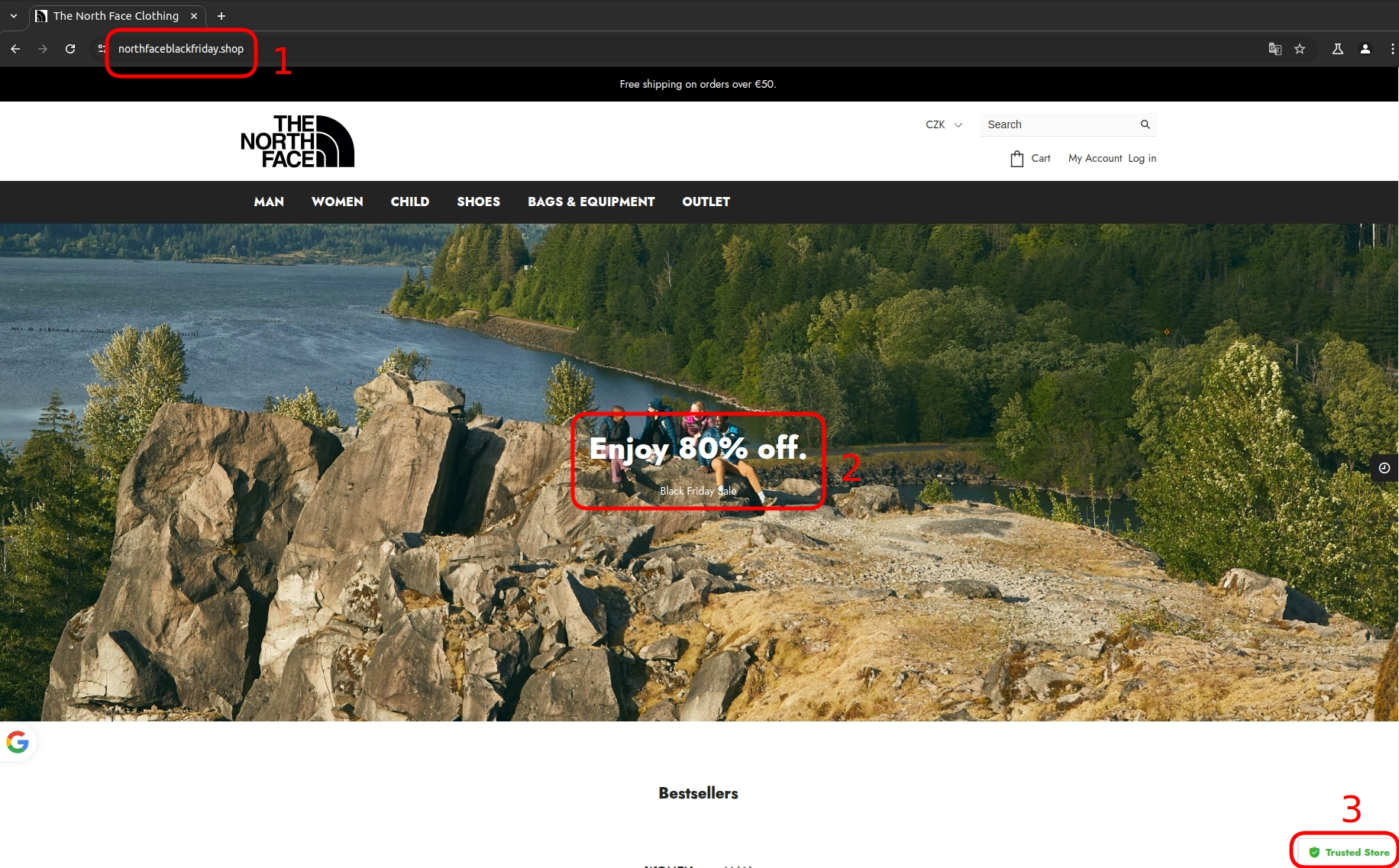
- Fake Facebook Page Kytary.cz : The Facebook page of the musical instrument store Kytary.cz was dealing with a fake version of itself. The fake page aimed to spread the post shown in the image below. The scammers even paid for promotion, which is why the label 'Sponsored' appeared under the false name 'Kytary CZ'.
🔐 Weak or Reused Passwords
Weak or reused passwords make it easy for attackers to gain access through brute-force or credential stuffing attacks. This can lead to identity theft, financial loss, and widespread compromise of personal or organizational accounts.
What to do:
- Use unique, complex and long password for each site. See: Latest Password Recommendation
- Turn on Two-Factor Authentication (2FA) wherever possible.
- Use a password manager to keep track safely.See: Start Using a Password Manager Today!
⚠️ Other threats to watch out for
- Beware of Crypto Scams : Cryptocurrency is a hot topic, attracting many people to invest with the promise of high returns. However, as interest grows, so do the number of scams.
- Fake articles that look like the truth – and could cost you a lot : Fake article mimicking the appearance of the news website Novinky.cz, which is spreading through social media.
- Quishing: The Rising Threat of QR Code Scams in Public Spaces : A scam where criminals place fake QR codes in public spaces, leading users to fraudulent websites that steal personal and financial details. This method is particularly effective at EV charging stations, parking meters, and other machines across Europe.
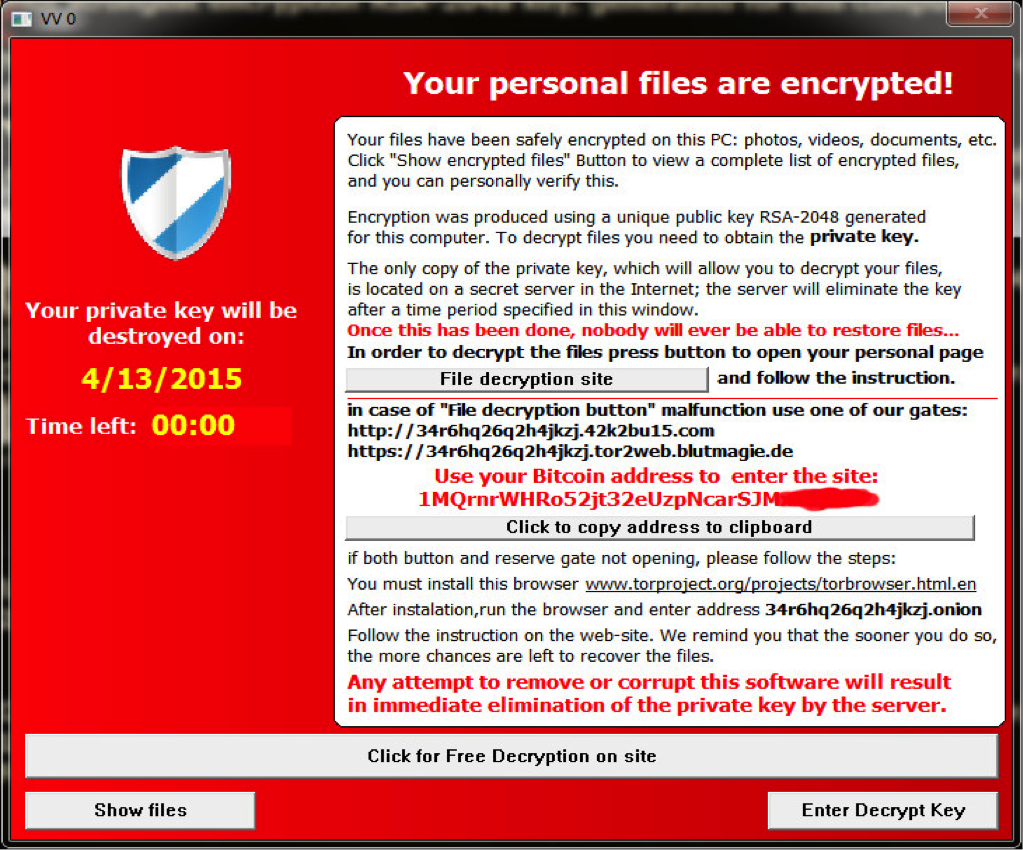
- Ransomware: A Growing Threat and How to Protect Yourself : In the world of cybersecurity, ransomware has emerged as one of the most damaging threats. It targets individuals, businesses, and organizations by encrypting their files or locking them out of their systems until a ransom is paid.
💡 Further recommendations and advice
- Backup your files periodically! See: Personal Data Backup .
- Make sure your smart devices are up to date. See: Smart Home: Beware of Outdated Devices .
- How to Stay Safe with Your Mobile Devices in Public : Your smartphone, laptop, or tablet is like a digital vault, carrying personal photos, financial information, and access to social media and bank accounts. Protecting it in public can prevent data theft, hacking, and physical loss.
- Stay informed! Read our blog and follow alerts in the app about the latest threats we’re monitoring for you.


